4 Step Cybersecurity Risk Assessment Infographic вђ Comcast Business

4 Step Cybersecurity Risk Assessment Infographic вђ Comcastођ Cast business 26 can helpexecutive summarythe. lobal cybersecurity community is at a crossroads.technology is accelerating faster than it ever has before, giving it and security teams more tools to fend off cybersecurity attacks. from an increasingly diverse slate of bad actors. however, the tactics attackers are using to access syste. In pursuit of convergence and operational relief, it leaders turn to sase. network and security must converge to face evolving threats and relieve stressed it teams. read more. 1. 2. learn how comcast business can help. keep you ready for what's next. insights, advice, and best practices to keep your business protected.
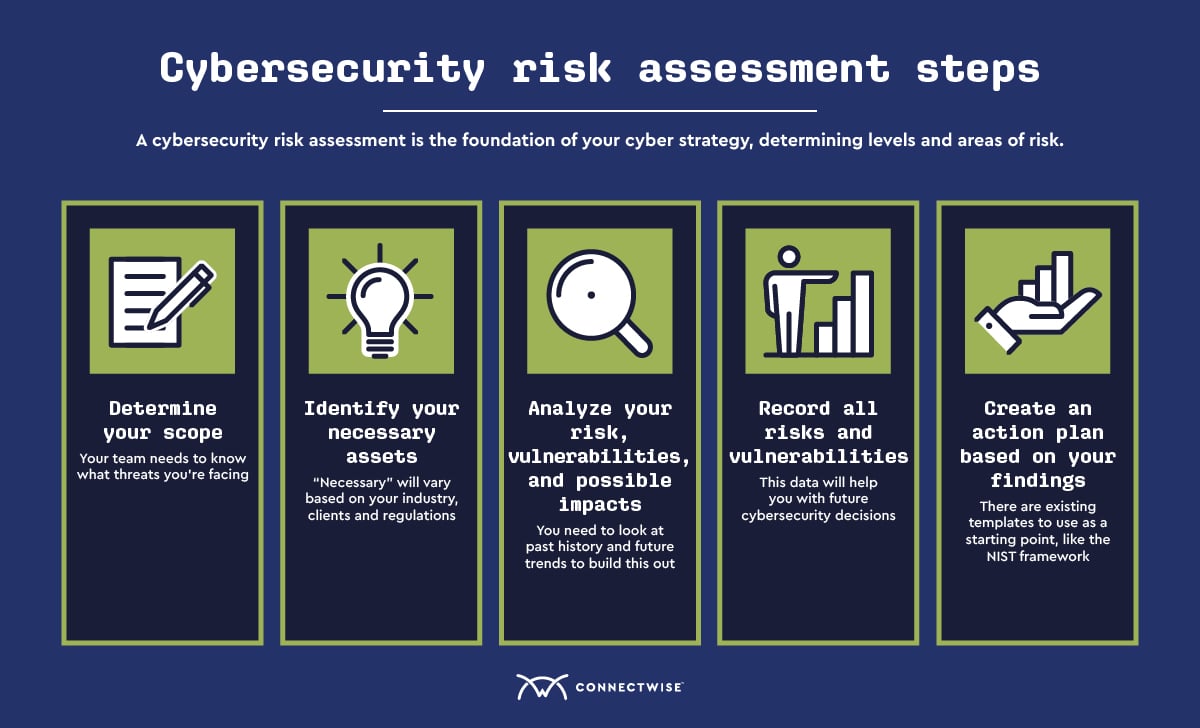
How To Conduct A Cybersecurity Risk Assessment Connectwise Step 1: determine the scope of the risk assessment. a risk assessment starts by deciding what is in scope of the assessment. it could be the entire organization, but this is usually too big an undertaking, so it is more likely to be a business unit, location or a specific aspect of the business, such as payment processing or a web application. 1. identify and prioritize assets. the first step is to survey your it environment and catalog the information and systems within it. a good place to start is to run an asset discovery scan, using some form of network of vulnerability scanning tool. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment. The planning stage of an it security risk assessment is crucial in identifying a business’ obligations, expectations, and key personnel responsible for ensuring the project goes smoothly. this means putting in place a process that clearly defines the project and how communication will be dealt with.

Comments are closed.