5 Steps To A Cybersecurity Risk Assessment Luminary Automation

5 Steps To A Cybersecurity Risk Assessment Luminary Automation Performing a cybersecurity risk assessment will give you greater knowledge and understanding of the potential threats that exist, and how they can harm your business. risk assessments can also help you: reduce costs; avoid financial loss ; strengthen your reputation with clients, vendors and business partners; step 1: take inventory of your. 5 steps to a cybersecurity risk assessment luminary automation, cybersecruity and engineering luminaryace.

Risk Assessment Process Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. 1. determining the scope of assessment. the first step in risk management is to determine the total scope of each assessment. while you could assess your entire organization, that is typically too big of an undertaking for one assessment. usually, it is best to start with a specific location, business unit, or business aspect. Step 5: report your findings. the goal of any risk assessment is to come out the other end with a final report that: provides a clear assessment of your current cyber security processes; outlines the risks and prioritises them in terms of severity; provides suggestions for improving, fixing, or modifying your systems and processes. Recognizing the types of data you hold and the sensitivity level of each sets the stage for your risk assessment. a data centric approach to cybersecurity flips the script. instead of a broad, one.
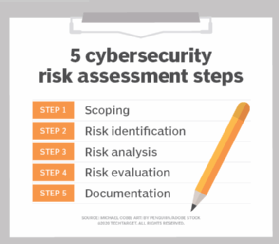
How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget Step 5: report your findings. the goal of any risk assessment is to come out the other end with a final report that: provides a clear assessment of your current cyber security processes; outlines the risks and prioritises them in terms of severity; provides suggestions for improving, fixing, or modifying your systems and processes. Recognizing the types of data you hold and the sensitivity level of each sets the stage for your risk assessment. a data centric approach to cybersecurity flips the script. instead of a broad, one. Step 1: catalog information assets. your risk management team should catalog all your business’s information assets. that includes your it infrastructure, as well as the various software as a service (saas), platform as a service (paas), and infrastructure as a service (iaas) solutions used throughout the company. Mark zuckerberg, the creator of facebook, once emphasized the significance of taking risks, stating, "the most significant risk is avoiding any risk. in a rapidly changing world, the only strategy destined to fail is avoiding risks." cybersecurity cannot be universally applied, as each organization confronts a distinct set of security risks, necessitating a tailored approach to cybersecurity.

5 Steps To A Cyber Security Risk Assessment Hostingb2b Step 1: catalog information assets. your risk management team should catalog all your business’s information assets. that includes your it infrastructure, as well as the various software as a service (saas), platform as a service (paas), and infrastructure as a service (iaas) solutions used throughout the company. Mark zuckerberg, the creator of facebook, once emphasized the significance of taking risks, stating, "the most significant risk is avoiding any risk. in a rapidly changing world, the only strategy destined to fail is avoiding risks." cybersecurity cannot be universally applied, as each organization confronts a distinct set of security risks, necessitating a tailored approach to cybersecurity.

Where To Start Nist

Comments are closed.