6 Steps To Cybersecurity Risk Assessment Methodology Cyber Security
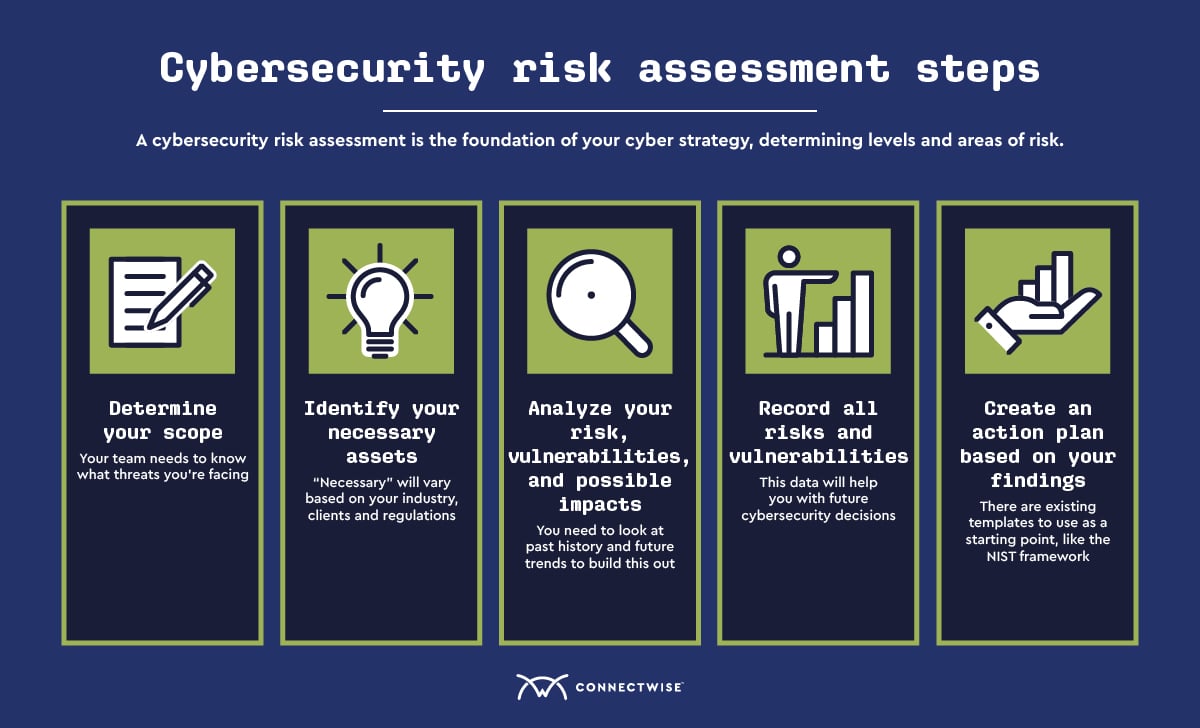
How To Conduct A Cybersecurity Risk Assessment Connectwise Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Cybersecurity (cyber) risk assessments assist public safety organizations in understanding the cyber risks to their operations (e.g., mission, functions, critical service, image, reputation), organizational assets, and individuals.1 to strengthen operational and cyber resiliency, safecom has developed this guide to assist public safety.
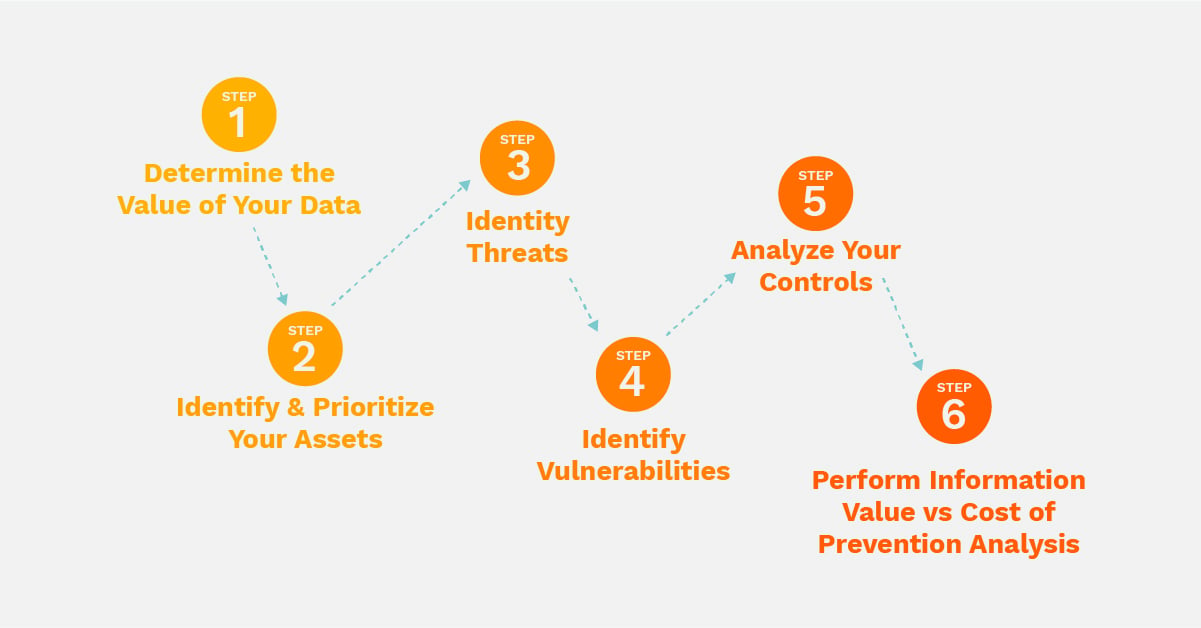
6 Steps To Cybersecurity Risk Assessment Methodology в Rktechtip 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization. Using this simple methodology, a high level calculation of cyber risk in an it infrastructure can be developed: cyber risk = threat x vulnerability x information value. download this post as a pdf >. imagine you were to assess the risk associated with a cyber attack compromising a particular operating system. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help. Step 2: identify and inventory assets. the next step is to identify and inventory the assets that are relevant to the risk assessment. this includes hardware, software, data, networks, and other resources that need to be protected. create a comprehensive inventory that outlines the criticality and value of each asset.

How To Perform A Cybersecurity Risk Assessment A Step By Step Guide A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help. Step 2: identify and inventory assets. the next step is to identify and inventory the assets that are relevant to the risk assessment. this includes hardware, software, data, networks, and other resources that need to be protected. create a comprehensive inventory that outlines the criticality and value of each asset. Security and risk teams must first identify which assets are most vulnerable by conducting a cybersecurity risk assessment to understand what risks exist and how to manage them. by regularly conducting risk assessments for cybersecurity, security professionals better understand what threats exist and what needs to be prioritized to decide a course of action for mitigating these risks. Cybersecurity risk assessments help organizations understand, control, and mitigate all forms of cyber risk. risk assessments are a critical component of a robust cyber risk management strategy. read this guide to learn: what is a cyber risk assessment; why perform cyber risk assessments, and who should be involved; step by step instructions.
How To Conduct A Cybersecurity Assessment Security and risk teams must first identify which assets are most vulnerable by conducting a cybersecurity risk assessment to understand what risks exist and how to manage them. by regularly conducting risk assessments for cybersecurity, security professionals better understand what threats exist and what needs to be prioritized to decide a course of action for mitigating these risks. Cybersecurity risk assessments help organizations understand, control, and mitigate all forms of cyber risk. risk assessments are a critical component of a robust cyber risk management strategy. read this guide to learn: what is a cyber risk assessment; why perform cyber risk assessments, and who should be involved; step by step instructions.
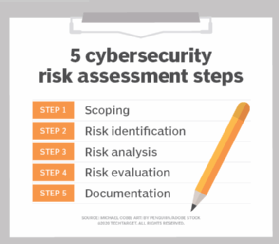
How To Perform A Cybersecurity Risk Assessment In 5 Steps News Itn

Comments are closed.