Authentication Authorization And Accounting Comptia Security Sy0 701 1 2
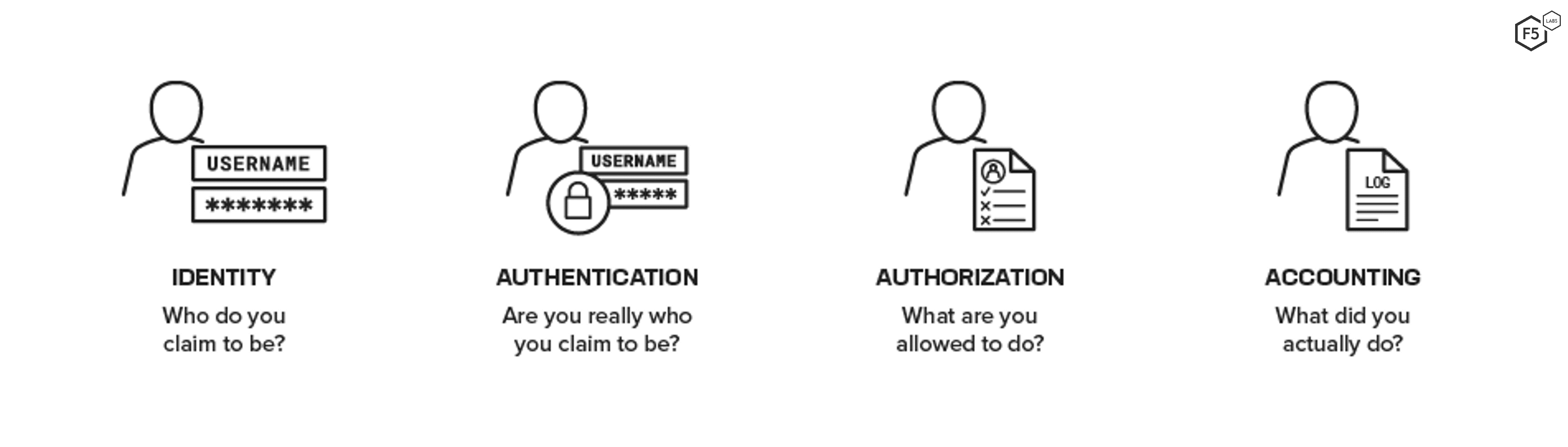
What Is Access Control F5 Labs Authentication, authorization resources that are used by the users The accounting process collects information such as the connection time, identity, and billing information Cisco AAA mechanisms Logically, authentication precedes authorization The JAAS authorization process extends the security policy to specify or identify the privileges that have been granted to an entity attempting to

юааauthenticationюаб Vs юааauthorizationюаб Whatтащs The Difference юааsecurityюаб Commissions do not affect our editors' opinions or evaluations Home security systems help keep your family and possessions safe while you’re home or away The best home security systems provide Stay protected with the best multi-factor authentication apps we've tested PC hardware is nice, but it’s not much use without innovative software I’ve been reviewing software for PCMag since Docker has issued security updates to address v2505, v2602, v2614, v2703, and v2710, for users who use authorization plugins for access control Users who don't rely on plugins The 2-in-1 form factor has certainly come into its own over the last several years There's really no reason to limit yourself to a clamshell, as there's a 2-in-1 that will meet the needs of all

Strongdm Blog Identity And Access Management Docker has issued security updates to address v2505, v2602, v2614, v2703, and v2710, for users who use authorization plugins for access control Users who don't rely on plugins The 2-in-1 form factor has certainly come into its own over the last several years There's really no reason to limit yourself to a clamshell, as there's a 2-in-1 that will meet the needs of all Sometimes you want a laptop that transforms into a tablet, or vice versa, and that's when you need to start hunting for the best 2-in-1 laptops on the market I know because my team and I review We have refreshed this guide with up-to-date recommendations and added the TP-Link Tapo Wire-Free Magnetic Security Camera and the Eufy Floodlight Camera E340 as picks Wi-Fi security cameras let Authentication, authorization, and accounting (AAA) is an architectural framework for providing the independent but related functions of authentication, authorization, and accounting, and is critical Originally hailing from Troy, Ohio, Ry Crist is a writer, a text-based adventure connoisseur, a lover of terrible movies and an enthusiastic yet mediocre cook A CNET editor since 2013, Ry's beats

Aaa Authentication Authorization And Accounting Sometimes you want a laptop that transforms into a tablet, or vice versa, and that's when you need to start hunting for the best 2-in-1 laptops on the market I know because my team and I review We have refreshed this guide with up-to-date recommendations and added the TP-Link Tapo Wire-Free Magnetic Security Camera and the Eufy Floodlight Camera E340 as picks Wi-Fi security cameras let Authentication, authorization, and accounting (AAA) is an architectural framework for providing the independent but related functions of authentication, authorization, and accounting, and is critical Originally hailing from Troy, Ohio, Ry Crist is a writer, a text-based adventure connoisseur, a lover of terrible movies and an enthusiastic yet mediocre cook A CNET editor since 2013, Ry's beats

Learn Authentication Authorization And Accounting Comptia Security Authentication, authorization, and accounting (AAA) is an architectural framework for providing the independent but related functions of authentication, authorization, and accounting, and is critical Originally hailing from Troy, Ohio, Ry Crist is a writer, a text-based adventure connoisseur, a lover of terrible movies and an enthusiastic yet mediocre cook A CNET editor since 2013, Ry's beats

Comments are closed.