Authentication Functions And 3 Ways To Produce Authentication Message Authentication

Authentication Functions Message authentication code (mac): a message authentication code is a security code that the user of a computer has to type in order to access any account or portal. these codes are recognized by the system so that it can grant access to the right user. these codes help in maintaining information integrity. it also confirms the authenticity of. A variation on the message authentication code is the one way hash function. as with the message authentication code, a hash function accepts a variable size message m as input and produces a fixed size output, referred to as a hash code h(m). unlike a mac, a hash code does not use a key but is a function only of the input message.
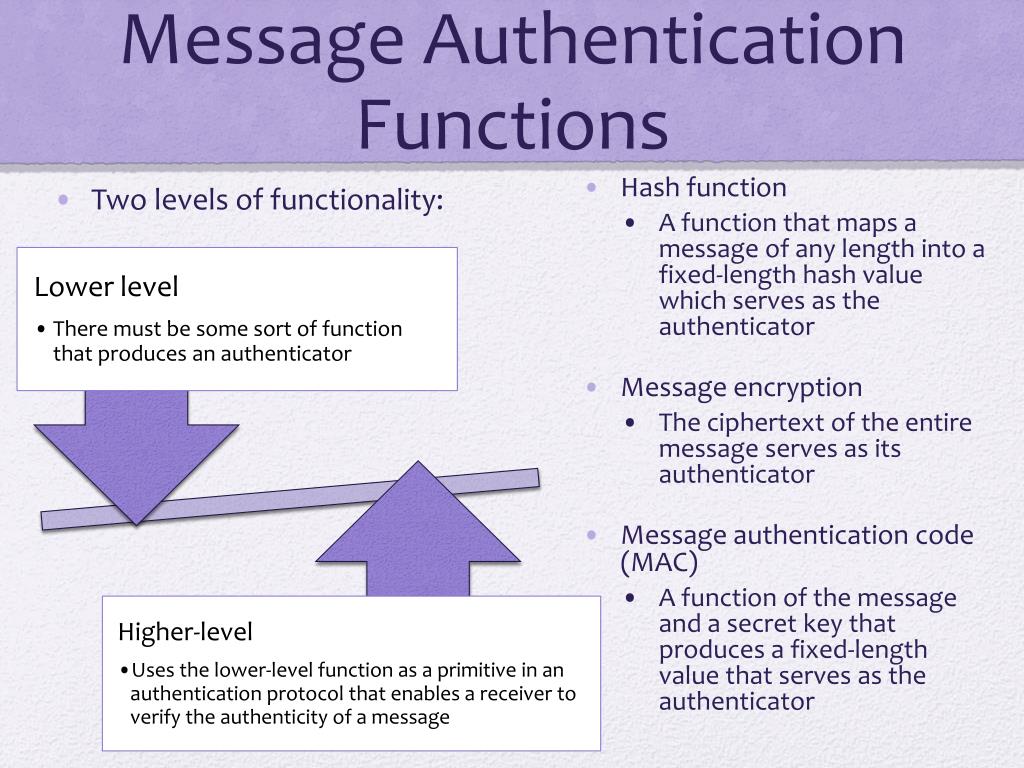
Ppt Message Authentication Requirements Powerpoint Presentation Free Message authentication code. in cryptography, a message authentication code ( mac ), sometimes known as an authentication tag, is a short piece of information used for authenticating and integrity checking a message. in other words, to confirm that the message came from the stated sender (its authenticity) and has not been changed (its integrity). Cture 15 of “computer andnetwork security” by avi kak)15.7.1 the sha family of hash fun. tionssha (secure hash algorithm) refers to a family of nist approved cryptographic h. the following table shows the various parameters of the different sha hash functions. algorithm message block word m essage security. Cryptographic hash functions hash functions. a hash function is a mathematical, efficiently computable function that has fixed size output: f : {0, 1}n. f: {0, 1}*. {0,1}n , where n > n {0,1}n. in cryptography, the first type of hash function is often called a compression function, with the name hash function reserved for the unbounded domain type. Message authentication or data origin authentication is an information security property that indicates that a message has not been modified while in transit ( data integrity) and that the receiving party can verify the source of the message. [ 1] message authentication does not necessarily include the property of non repudiation. [ 2][ 3].

What S The Best Authentication Method Analysis 2024 Cryptographic hash functions hash functions. a hash function is a mathematical, efficiently computable function that has fixed size output: f : {0, 1}n. f: {0, 1}*. {0,1}n , where n > n {0,1}n. in cryptography, the first type of hash function is often called a compression function, with the name hash function reserved for the unbounded domain type. Message authentication or data origin authentication is an information security property that indicates that a message has not been modified while in transit ( data integrity) and that the receiving party can verify the source of the message. [ 1] message authentication does not necessarily include the property of non repudiation. [ 2][ 3]. Construct a distinguisher and compute its advantage. hint: request a mac on two single block messages, then use the result to forge the mac of a two block message. 11.6: let e be a cpa secure encryption scheme and m be a secure mac. show that the following encryption scheme (called encrypt & mac) is not cca secure:. Here we need to detect the falsification in the message b has got. here a will create a key (used to create message authentication code) and sends the key to b. a will create a value using ciphertext and key and the value is obtained. this value created by ciphertext key = message authentication code. b has to check whether the ciphertext is.

What Is Authentication Types Of Authentication Construct a distinguisher and compute its advantage. hint: request a mac on two single block messages, then use the result to forge the mac of a two block message. 11.6: let e be a cpa secure encryption scheme and m be a secure mac. show that the following encryption scheme (called encrypt & mac) is not cca secure:. Here we need to detect the falsification in the message b has got. here a will create a key (used to create message authentication code) and sends the key to b. a will create a value using ciphertext and key and the value is obtained. this value created by ciphertext key = message authentication code. b has to check whether the ciphertext is.

Comments are closed.