Conducting A Cybersecurity Risk Assessment

How To Perform A Cybersecurity Risk Assessment A Step By Step Guide Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help.
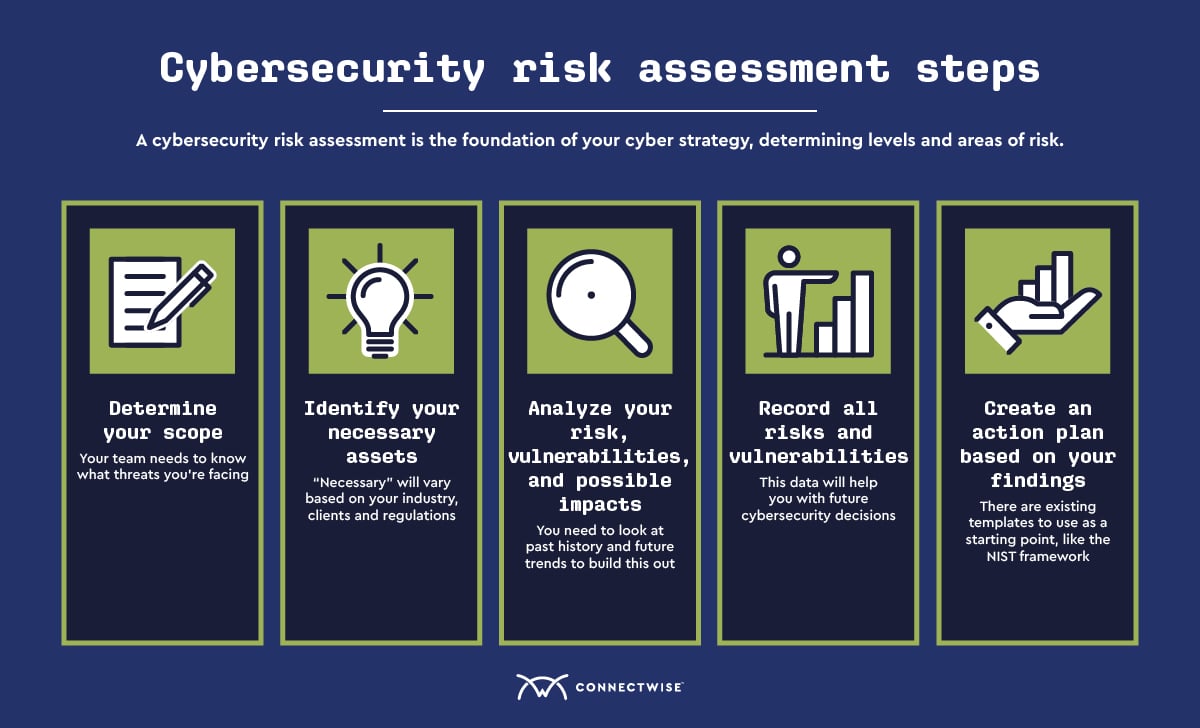
How To Conduct A Cybersecurity Risk Assessment Connectwise Included with this guide are customizable reference tables (pages two, three, and four) to help organizations identify and document personnel and resources involved with each step of the assessment. while example entities and organizations are provided, customization is advised. 2. by conducting cyber risk assessments, public safety. 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization. Conducting basic risk assessments. there are numerous ways to conduct a cybersecurity risk assessment and organizations can mature their process over time to consider additional inputs in the assessment process (see advancing risk assessments over time below). the methodology below aligns to the functionality included in crosscomply. it is a. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment.
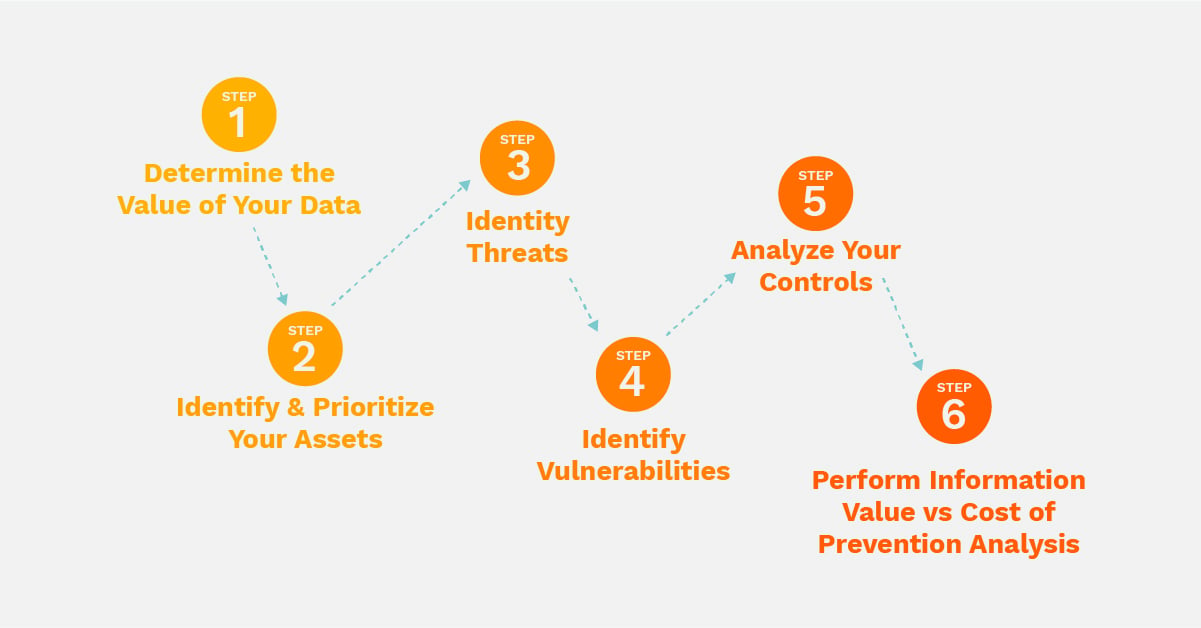
How To Conduct A Cybersecurity Assessment Conducting basic risk assessments. there are numerous ways to conduct a cybersecurity risk assessment and organizations can mature their process over time to consider additional inputs in the assessment process (see advancing risk assessments over time below). the methodology below aligns to the functionality included in crosscomply. it is a. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment. Conducting a cybersecurity risk assessment is a critical step in protecting an organization’s information assets from cyber threats. by following a systematic approach and using the right tools and templates, organizations can identify vulnerabilities, assess risks, and implement effective risk mitigation strategies. Security and risk teams must first identify which assets are most vulnerable by conducting a cybersecurity risk assessment to understand what risks exist and how to manage them. by regularly conducting risk assessments for cybersecurity, security professionals better understand what threats exist and what needs to be prioritized to decide a.

Conducting A Cybersecurity Risk Assessment Youtube Conducting a cybersecurity risk assessment is a critical step in protecting an organization’s information assets from cyber threats. by following a systematic approach and using the right tools and templates, organizations can identify vulnerabilities, assess risks, and implement effective risk mitigation strategies. Security and risk teams must first identify which assets are most vulnerable by conducting a cybersecurity risk assessment to understand what risks exist and how to manage them. by regularly conducting risk assessments for cybersecurity, security professionals better understand what threats exist and what needs to be prioritized to decide a.
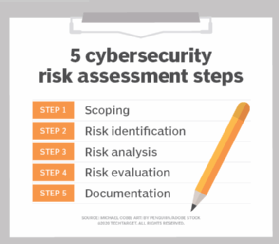
How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget

Comments are closed.