Cyber Attack Cheat Sheet Infographic

Cyber Security Encryption Cheat Sheet Cyber attack cheat sheet. by david wallace | apr 15, 2020 | internet infographics. cybercrime is the fastest kind of crime growing in the united states as well as around the world. in the case of cyber attacks, prevention is the best line of defense. securing networks, data, and devices from attack requires knowledge of how these different. This infographic from mindtrades consulting takes a closer look at this threat:you may also want to see: coffee & […] cyber attack cheat sheet infographic best infographics create viral videos with ai plenty of businesses have become a victim of cyber attacks.
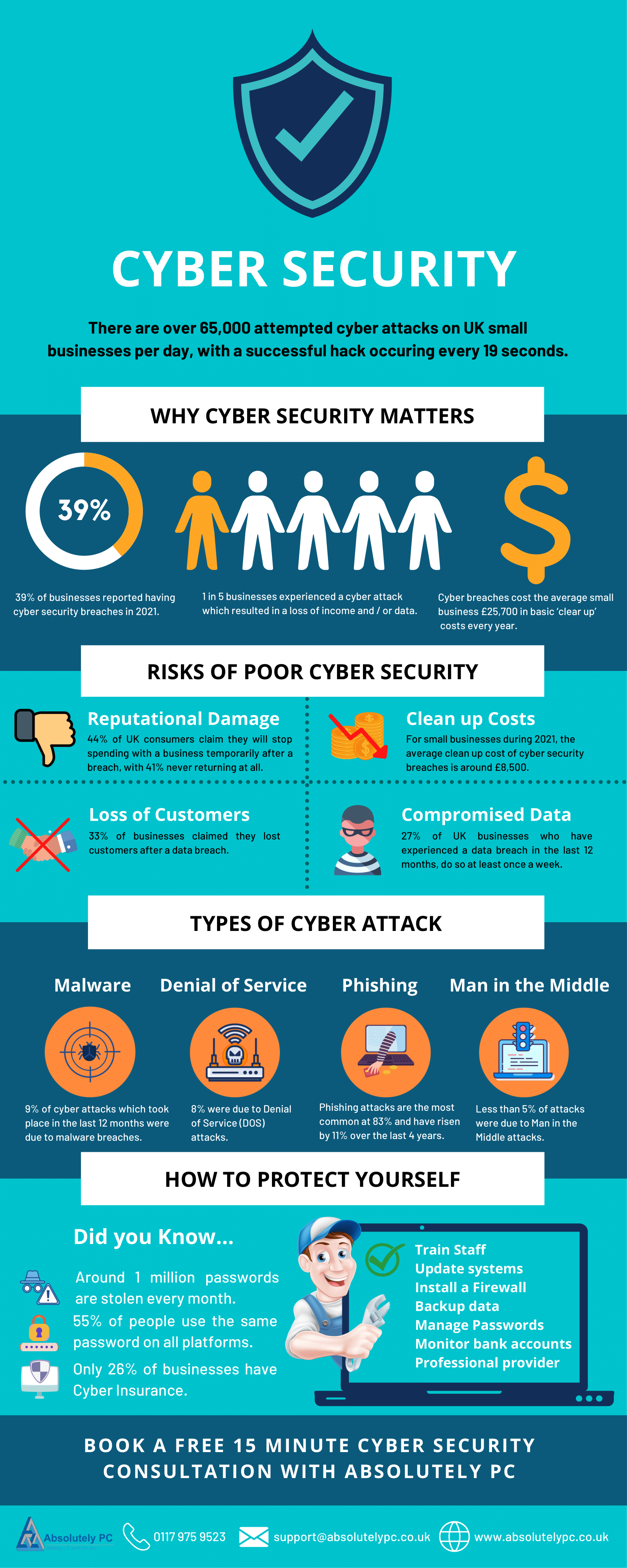
Why Cyber Security Matters Infographic Absolutely Pc Amazon : cyber attack cheat sheet: an infographic ebook ebook : team, techfastly: kindle store. Tcp syn flood attack: place the servers behind a firewall and stop inbound syn packets teardrop attack: disable smbv2 and block ports 139 and 445 smurf attack: disable ip directed broadcasts at the routers ping of death attacks: use a firewall that checks fragmented ip packets for maximum size botnets: use black hole filtering, which drops. Asset. assets are anything that a cyber security strategy should protect. it can be both physical and digital assets ranging from physical computer machines to softwares and data that needs to be protected. access control (ac) the selective restriction of access to users on a certain platform, application, or software. A cybersecurity cheat sheet is a quick reference document that provides access to critical information related to cybersecurity procedures, commands, tools, and guidelines to help information security professionals. some examples of data that may be included in a cybersecurity cheat sheet are the following: 2.

Cyber Attack Cheat Sheet An Infographic Ebook Ebook Team Techfastly Asset. assets are anything that a cyber security strategy should protect. it can be both physical and digital assets ranging from physical computer machines to softwares and data that needs to be protected. access control (ac) the selective restriction of access to users on a certain platform, application, or software. A cybersecurity cheat sheet is a quick reference document that provides access to critical information related to cybersecurity procedures, commands, tools, and guidelines to help information security professionals. some examples of data that may be included in a cybersecurity cheat sheet are the following: 2. Top 7 attacks your organization should watch out for in 2023 (cybersecurity infographics) 1) multi factor authentication (mfa) attack. 2) hardware and software vulnerabilities. 3) shadow apis. 4) attacks through mobile devices. 5) the digital supply chain assault. 6) ransomware. 7) persistent phishing. Cybersecurity: skimming. in cybersecurity, skimming refers to a physical attack technique which uses a fake card reader in order to skim, or copy, a smart card’s data. this can include id cards, credit cards, and other smart cards. skimming is an example of a physical attack because skimmers rely on proximity to smart cards or installation on.

Cybersecurity Awareness A Simple Cheat Sheet For Staying Safe Top 7 attacks your organization should watch out for in 2023 (cybersecurity infographics) 1) multi factor authentication (mfa) attack. 2) hardware and software vulnerabilities. 3) shadow apis. 4) attacks through mobile devices. 5) the digital supply chain assault. 6) ransomware. 7) persistent phishing. Cybersecurity: skimming. in cybersecurity, skimming refers to a physical attack technique which uses a fake card reader in order to skim, or copy, a smart card’s data. this can include id cards, credit cards, and other smart cards. skimming is an example of a physical attack because skimmers rely on proximity to smart cards or installation on.

Comments are closed.