Cyber Security Risk Assessment A Step By Step Method To Perform Cybersecurity Risk Assessment

How To Perform A Cybersecurity Risk Assessment A Step By Step Gu Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Here are seven key steps for conducting a comprehensive cyber risk assessment. 1. perform a data audit and prioritize based on value. establishing a comprehensive and current asset inventory is a foundational element of every company’s cybersecurity program.
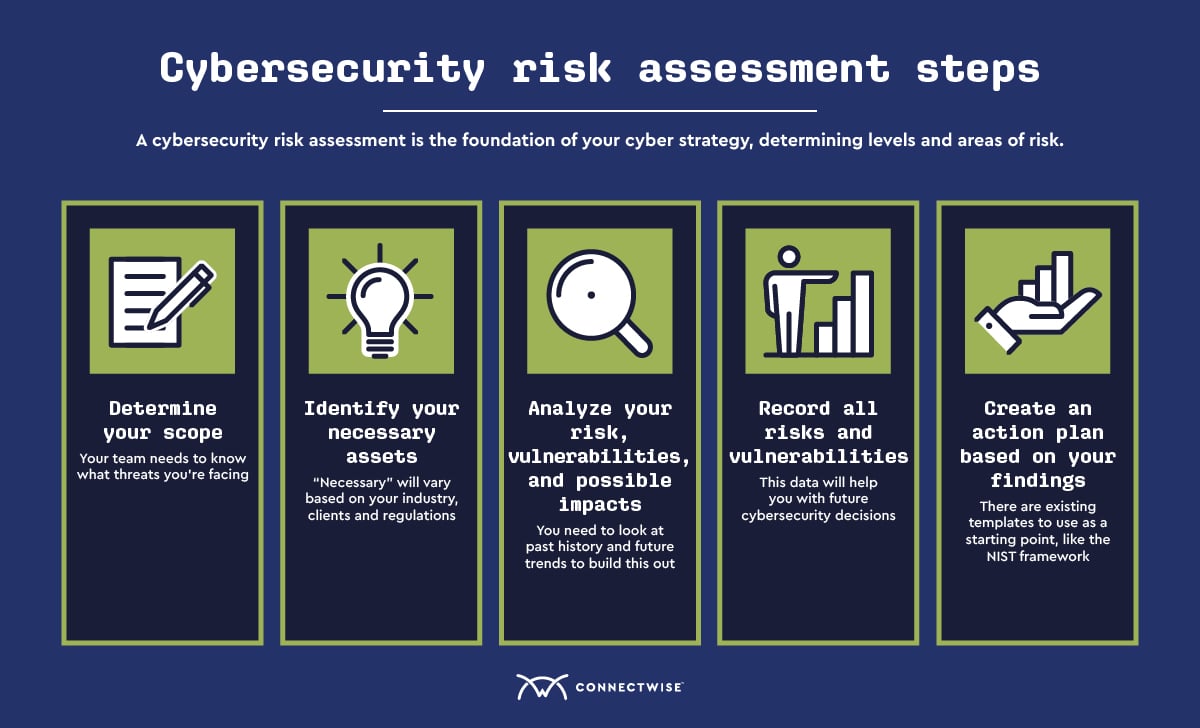
How To Conduct A Cybersecurity Risk Assessment Connectwise Cybersecurity (cyber) risk assessments assist public safety organizations in understanding the cyber risks to their operations (e.g., mission, functions, critical service, image, reputation), organizational assets, and individuals.1 to strengthen operational and cyber resiliency, safecom has developed this guide to assist public safety. How to perform a cybersecurity risk assessment. identify and prioritize assets: identify all critical assets, including hardware, software, data, and intellectual property. categorize them based on their importance and value to the organization to prioritize risk assessment efforts. Step 8: document results from risk assessment reports. the final step is to develop a risk assessment report to support management in deciding on budgets, policies, and procedures. the report should describe the risk, vulnerabilities, and value of each threat, along with the impact and likelihood of occurrence and control recommendations. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help.

How To Perform A Cyber Security Risk Assessment Step By Step Gui Step 8: document results from risk assessment reports. the final step is to develop a risk assessment report to support management in deciding on budgets, policies, and procedures. the report should describe the risk, vulnerabilities, and value of each threat, along with the impact and likelihood of occurrence and control recommendations. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help. Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses. Step 2: identify and inventory assets. the next step is to identify and inventory the assets that are relevant to the risk assessment. this includes hardware, software, data, networks, and other resources that need to be protected. create a comprehensive inventory that outlines the criticality and value of each asset.
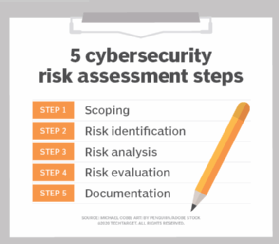
How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses. Step 2: identify and inventory assets. the next step is to identify and inventory the assets that are relevant to the risk assessment. this includes hardware, software, data, networks, and other resources that need to be protected. create a comprehensive inventory that outlines the criticality and value of each asset.

How To Perform A Cyber Security Risk Assessment A Step By Step G

Comments are closed.