Cybercrime Attacks The 5 Most Common Types Wp Farm

Cybercrime Attacks The 5 Most Common Types Wp Farm Here are 5 of the most common types of cyber attacks: denial of service (dos) password attack. sql injection. phishing. man in the middle (mitm) attacks. regardless of whether you’re a full fledged jedi or a padawan, you’re going to need to know about the various hacker threats that are out there. Aside from those above, there are certainly other cyberattack types worth worrying about: rootkits that are subtly implanted to steal or corrupt data, formjacking of payment details, 5 cross site scripting (a cousin to sql injection) and more. but the five bulleted exploit classes should absolutely be at the top of any organization's threat.
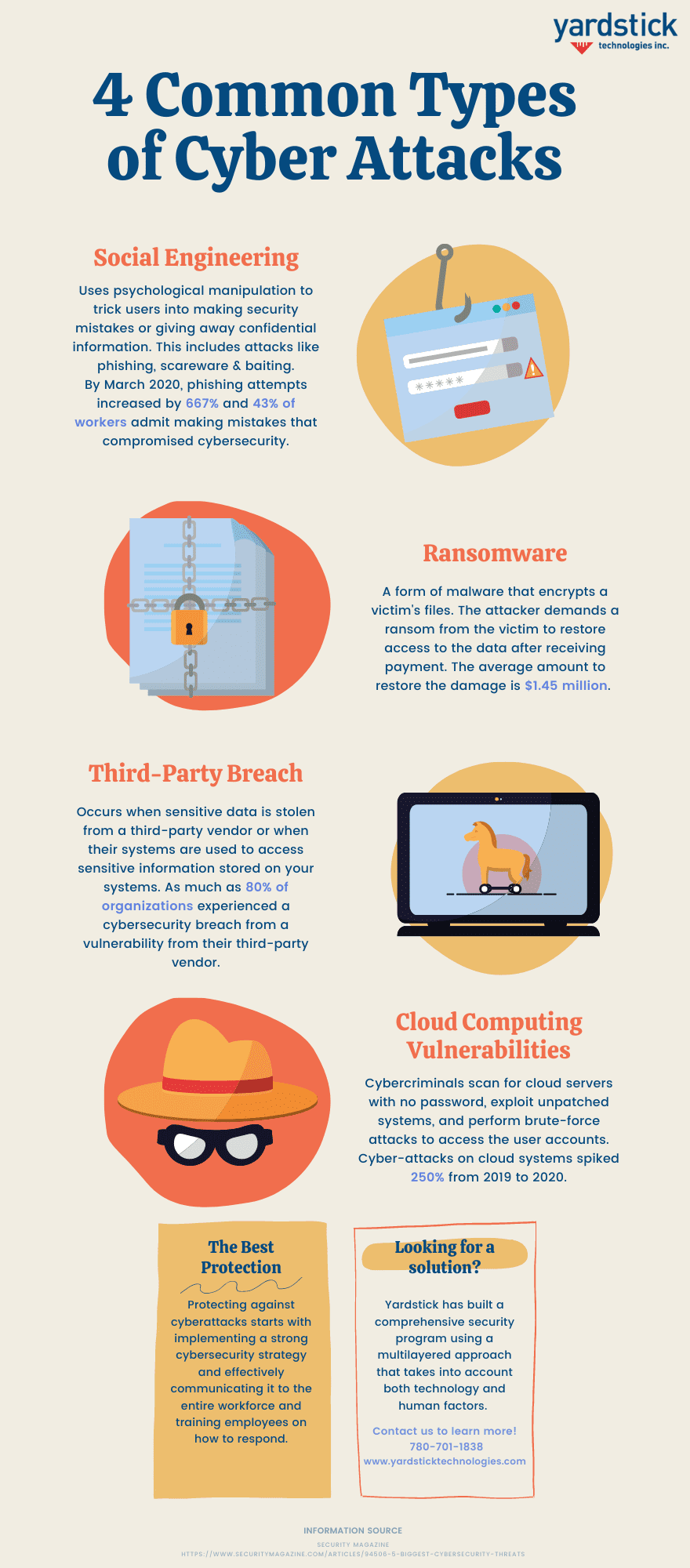
4 Common Cyber Attacks Infographic 1. malware. malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server. malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any. Implement content security policy (csp) headers to specify which forms of content are trusted on your site. educate users about the dangers of social engineering tactics. 2. sql injection attacks. sql injection is a serious attack that can compromise the integrity and confidentiality of a website’s database. 3. sql injection attacks. one of the most common wordpress attacks, an individual may cause damage or gain access to your wordpress admin by injecting malicious sql queries or statements to manipulate your mysql database. any user input section of your wordpress site such as a contact form or search box may be susceptible to a sql injection attack. Five years later, phishing has become the most prevalent cyber attack. this past year, more than half of criminal online activity was connected to this long running type of cyber crime.
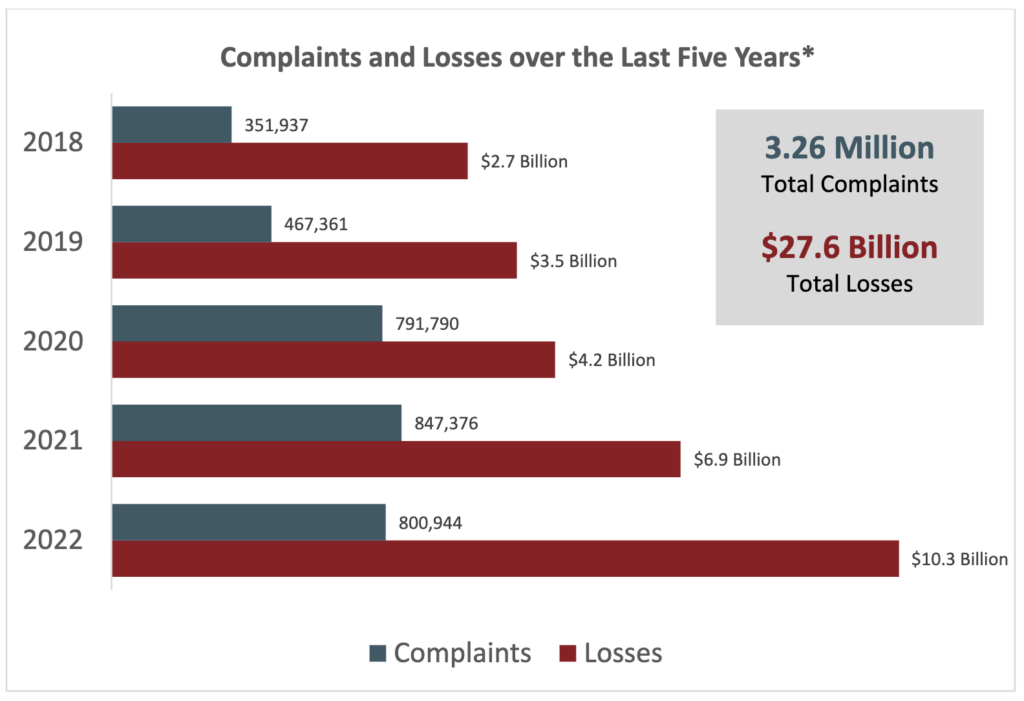
Cybercrime Losses Exceeded 10 Billion In 2022 Fbi Securityweek 3. sql injection attacks. one of the most common wordpress attacks, an individual may cause damage or gain access to your wordpress admin by injecting malicious sql queries or statements to manipulate your mysql database. any user input section of your wordpress site such as a contact form or search box may be susceptible to a sql injection attack. Five years later, phishing has become the most prevalent cyber attack. this past year, more than half of criminal online activity was connected to this long running type of cyber crime. Statistics show that the average ddos attack costs around $20,000 $40,000 per hour. other than denial of service (dos) attacks, we also have distributed denial of service (ddos) attacks. while dos attacks overflow a system’s resources from one location to prevent it from responding to service requests, the ddos attack method is somewhat. 5. cryptojacking. cryptojacking refers to a hacker’s covert efforts to commandeer a computer’s processing power for the purpose of mining cryptocurrencies, like bitcoin and ether, while the user is unaware or non consenting. jeopardized systems suffer a slow processing speed. 6.

Read Share The Costliest Types Of Cyber Crime Community Statistics show that the average ddos attack costs around $20,000 $40,000 per hour. other than denial of service (dos) attacks, we also have distributed denial of service (ddos) attacks. while dos attacks overflow a system’s resources from one location to prevent it from responding to service requests, the ddos attack method is somewhat. 5. cryptojacking. cryptojacking refers to a hacker’s covert efforts to commandeer a computer’s processing power for the purpose of mining cryptocurrencies, like bitcoin and ether, while the user is unaware or non consenting. jeopardized systems suffer a slow processing speed. 6.
Cybercrime Attacks The 5 Most Common Types Wp Farm

Comments are closed.