Cybersecurity Risk Assessment Create Your First One Now Liquid Web
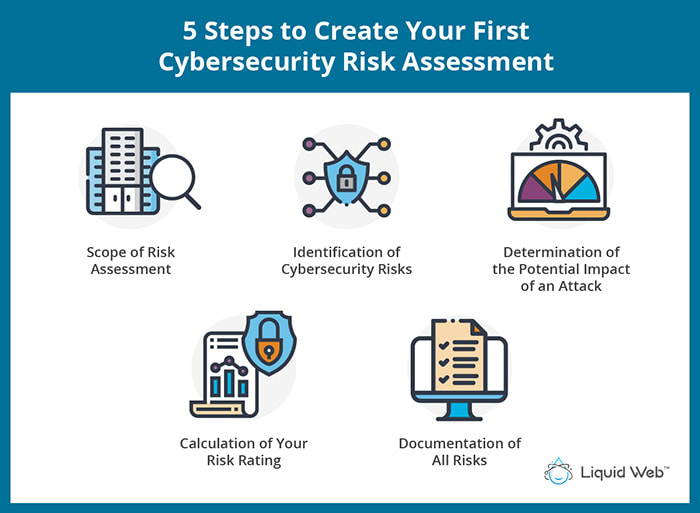
Cybersecurity Risk Assessment Create Your First One Now Liquid Web 5 steps to create your first cybersecurity risk assessment. a cybersecurity risk assessment must include scoping, risk identification, risk analysis, risk evaluation, and documentation. 1. scope of risk assessment. decide what is included in the scope of the risk evaluation. the scope can consist of a particular department, unit, or the entire. Therefore, establishing protocols for relaying information between team members, other staff, and external stakeholders like security agencies, service providers, and clients is essential to your plan’s success. 7. test, review, and improve. the constantly evolving threat landscape means you need to regularly test your incident response plan.

Cybersecurity Risk Assessment Create Your First One Now Liquid Web The risk assessment results will determine your organization’s readiness to respond to security events and uncover your infrastructure’s vulnerabilities to common attacks like phishing, malware, brute force attacks, and ransomware. how to mitigate security risk: any cybersecurity risk assessment should include the following five steps:. A cybersecurity risk assessment is a process organizations go through to identify, categorize, and respond to security risks. this could include unpatched vulnerabilities, poor access controls, phishing – and much more. the goal is to get an understanding of your overall risk threshold, so you can identify strategies and policies to help. Cybersecurity (cyber) risk assessments assist public safety organizations in understanding the cyber risks to their operations (e.g., mission, functions, critical service, image, reputation), organizational assets, and individuals.1 to strengthen operational and cyber resiliency, safecom has developed this guide to assist public safety. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given.

Top 6 Cybersecurity Risk Assessment Templates And Tip Vrogue Co Cybersecurity (cyber) risk assessments assist public safety organizations in understanding the cyber risks to their operations (e.g., mission, functions, critical service, image, reputation), organizational assets, and individuals.1 to strengthen operational and cyber resiliency, safecom has developed this guide to assist public safety. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization’s it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment.

Top 6 Cybersecurity Risk Assessment Templates And Tip Vrogue Co A cybersecurity risk assessment is a systematic process aimed at identifying vulnerabilities and threats within an organization’s it environment, assessing the likelihood of a security event, and determining the potential impact of such occurrences. in most cases, a risk assessment will also provide recommendations for additional security. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment.

5 Steps To Create Your Own Cybersecurity Risk Assessment 1591163680

Comments are closed.