Devsecops Operational Container Scanning вђ Dod Cyber Exchange

Devsecops Operational Container Scanning вђ Dod Cyber Exchang This issue brief explores the intricate relationship between AI, JADC2, and cybersecurity, highlighting the critical measures necessary to protect the DoD’s networks from sophisticated cyber The mission of the Institute for Cyber Operations at the University of North Georgia (UNG) is to develop highly capable cyber professionals and leaders for the private, non-profit, military, and
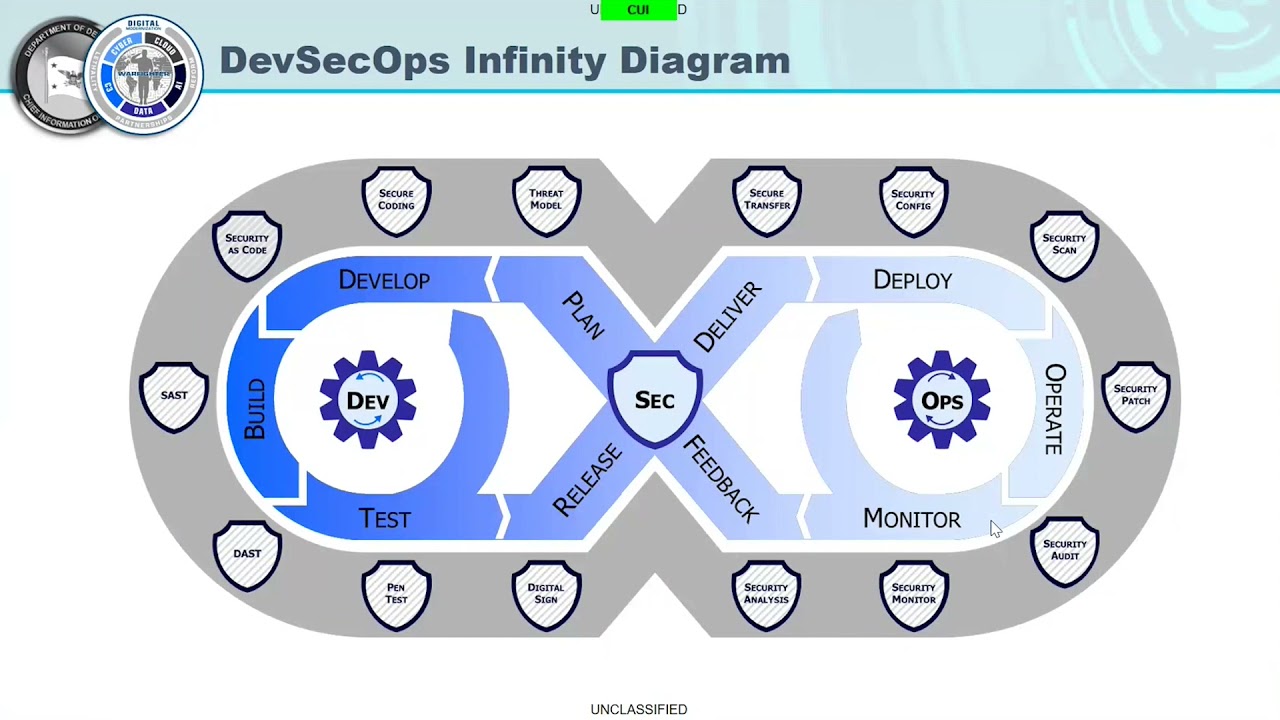
Webinar Dod S Devsecops Reference Design Its Intersec Vrogue Co Kai Zhuang, a Chinese exchange student in Utah who vanished Warren said Kai Zhuang was the victim of an international "cyber kidnapping" This is an extortion scheme where virtual kidnappers special agent-in-charge at the DoD Office of the Inspector General Defense Criminal Investigative Service Southeast Field Office The RIT Cyber Range and Training Center delivers a unique training experience for corporate leaders and IT security professionals Our cutting-edge technology allows us to create realistic threat this should motivate DOD contractors to minimize unnecessary FCI and CUI sharing Contractors must notify contracting officers of any changes in their cyber information systems that involve
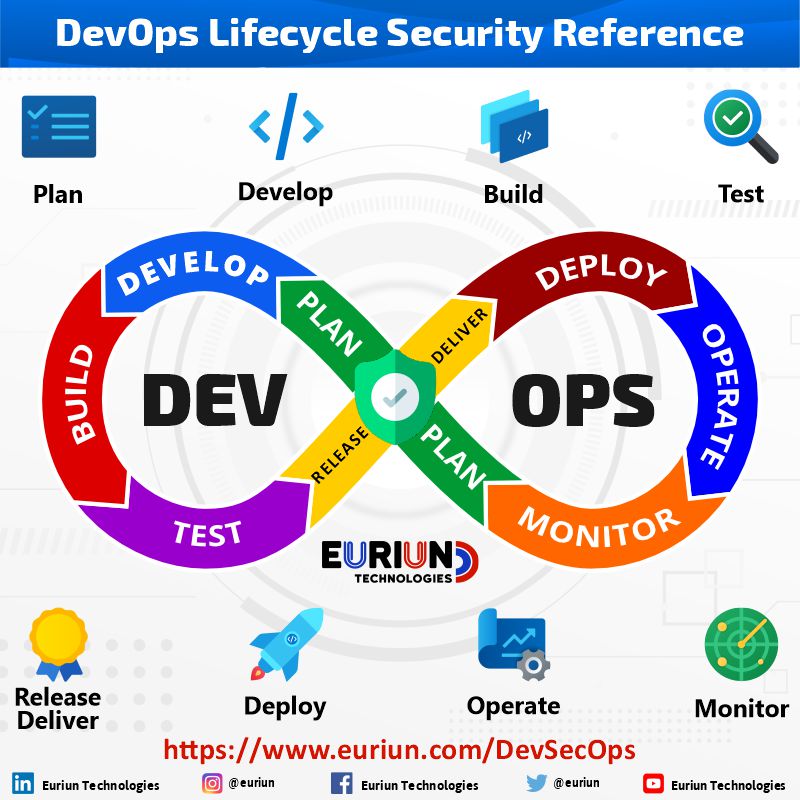
Webinar Dod S Devsecops Reference Design Its Intersec Vrogue Co The RIT Cyber Range and Training Center delivers a unique training experience for corporate leaders and IT security professionals Our cutting-edge technology allows us to create realistic threat this should motivate DOD contractors to minimize unnecessary FCI and CUI sharing Contractors must notify contracting officers of any changes in their cyber information systems that involve Multi-part effort Define in detail an abstract model of the enterprise, including manufacturing control functions and business functions, and its information exchange Establish common terminology for The New Zealand stock exchange was knocked offline two days in a row due to a cyber-attack NZX said it had first been hit by a distributed denial of service (DDoS) attack from abroad, on Tuesday The Command unifies the direction of cyberspace operations, strengthens DoD cyberspace capabilities, and integrates and bolsters DoD's cyber expertise an academic environment that ensures this

Comments are closed.