Dod Cyberspace Establishing A Shared Understanding And How To Protect
Dod Cyberspace Establishing A Shared Understanding And How To Protect Yet, there is a lack of shared understanding about cyberspace across the dod and the joint force and even less understanding of how the dod should protect its cyberspace. despite a desire to understand cyberspace and to protect ourselves, a dearth of clear, concise guidance for the joint force has led to a lack of emphasis on cyberspace and cyberspace security in planning and operations. This article establishes a clear, shared understanding of dod cyberspace, provides guidance to the dod to protect its cyberspace, and illustrates current and dod cyberspace: establishing a shared understanding and how to protect it us cyber command members work in the integrated cyber center at the joint operations center in fort george g.

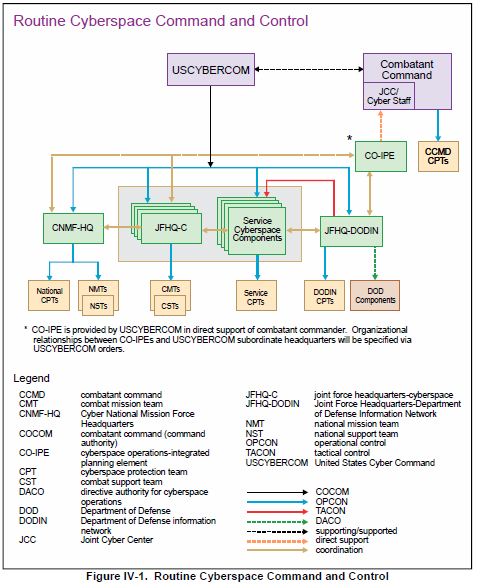
Dod Cyberspace Establishing A Shared Understanding And How To Protect Dod cyberspace: establishing a shared understanding and how to protect it the full consequences of potential adversary cyberspace operations (co) in the dod are still being fully understood. yet, there is a lack of shared understanding about cyberspace across the dod and the joint force and even less understanding of how the dod should protect its cyberspace. Specifically, the strategy identified five strategic initiatives: organize the defense department to “take full advantage of cyberspace’s potential”; protect the dod’s networks and systems; partner with other elements in the federal government and private sector; strengthen collective cybersecurity internationally with allies and partners; and build an effective workforce and enable. Cyberspace defense actions are conducted by the commander with authority over the information environment to protect, detect, characterize, counter, and mitigate threats and vulnerabilities. cyberspace isr is normally authorized under military authorities and conducted to provide critical operational information to support follow on actions. The 2023 dod cyber strategy is grounded in real world experience. since 2018, the department has conducted a significant number of cyberspace operations through its policy of defending forward, actively disrupting malicious cyber activity before it can affect the u.s. homeland. this strategy is.
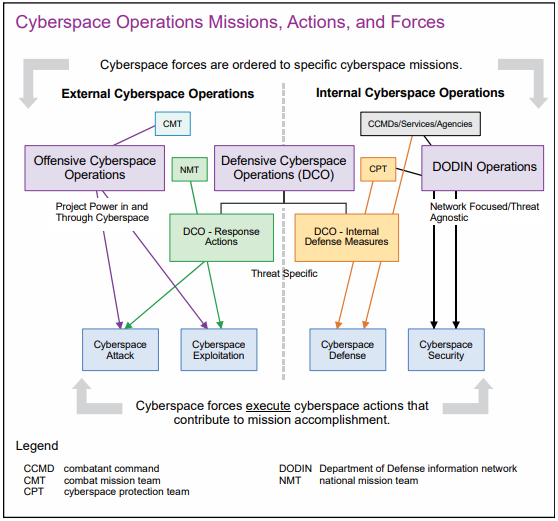
Dod Cyberspace Establishing A Shared Understanding And How To Protect Cyberspace defense actions are conducted by the commander with authority over the information environment to protect, detect, characterize, counter, and mitigate threats and vulnerabilities. cyberspace isr is normally authorized under military authorities and conducted to provide critical operational information to support follow on actions. The 2023 dod cyber strategy is grounded in real world experience. since 2018, the department has conducted a significant number of cyberspace operations through its policy of defending forward, actively disrupting malicious cyber activity before it can affect the u.s. homeland. this strategy is. Cyberspace is critical to the way the entire u.s. functions. in september, the white house released a new national cyber strategy based on four pillars. Dod cyberspace: establishing a shared understanding and how to protect it. the full consequences of potential adversary cyberspace operations (co) in the dod are still being fully understood. yet, there is a lack of shared understanding about cyberspace across the dod and the joint force and even less understanding of how the dod should protect.

Comments are closed.