Five Years Information Security Roll Out Roadmap Template Powerp

Five Years Information Security Transformation Roadmap Template Presenting five years information security roll out roadmap template powerpoint slide. this ppt theme is available in both 4,3 and 16,9 aspect ratios. this powerpoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. Template 1: five years information technology security roadmap template. use this powerpoint template to create a five year it security roadmap for your business. this action plan depicts the series of steps to be taken from 2021 2025 to ensure protection of your organization’s assets.
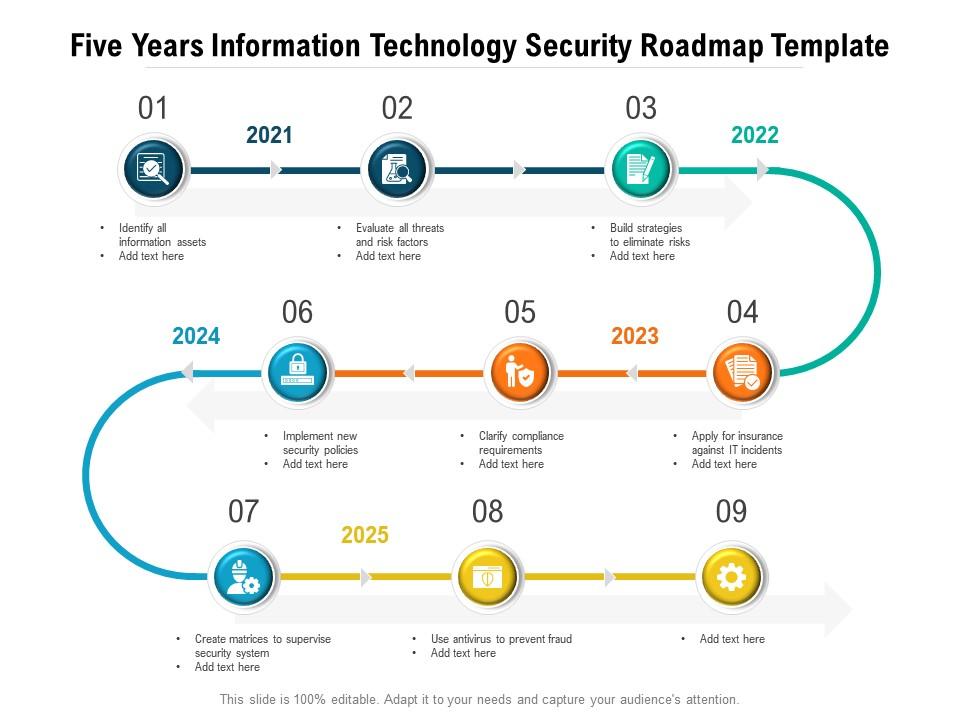
Five Years Information Technology Security Roadmap Template Presenting five years information security transformation roadmap template powerpoint slide. this ppt presentation is google slides compatible hence it is easily accessible. this ppt theme is available in both 4,3 and 16,9 aspect ratios. We present our 5 year business security service it system implementation roadmap information. this powerpoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. in addition to this, the powerpoint layout is google slides compatible, so you can share it with your audience and give them access to. Professionally designed, visually stunning five years data safety roll out roadmap template ideas. toggle nav. search. search. search. 5. notifications 5. Roadmap template. figure 3: roadmap template the intent of a roadmap is to document the activities projects by calendar year, typically three to five years. the focus of the activities is to meet the strategic objectives. the activities should include technology, processes, and or procedures and measures of success.
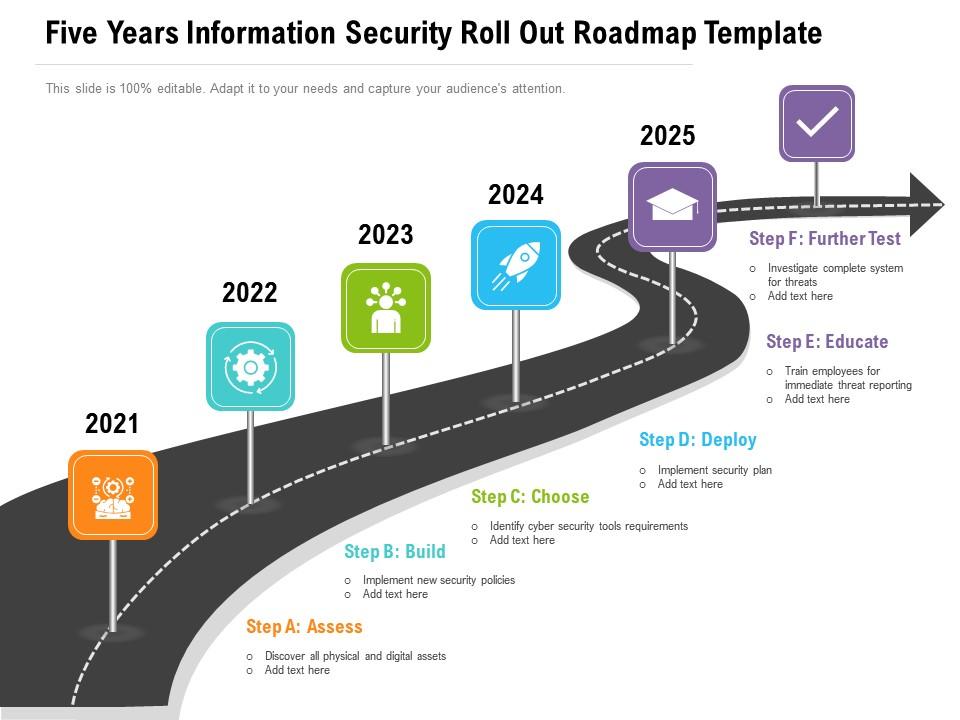
Quarterly Information Security Roll Out Roadmap Templ Vrogue Co Professionally designed, visually stunning five years data safety roll out roadmap template ideas. toggle nav. search. search. search. 5. notifications 5. Roadmap template. figure 3: roadmap template the intent of a roadmap is to document the activities projects by calendar year, typically three to five years. the focus of the activities is to meet the strategic objectives. the activities should include technology, processes, and or procedures and measures of success. Powerpoint 6 month product roadmap template. download the 6 month product roadmap template for powerpoint. when to use this template: product managers and team leads can use this template to communicate a product’s high level goals, initiatives, and timeline over a six month period. this template is best suited for kickoff meetings, progress. A cyber security strategy includes an integrated strategy to reduce cyber risks by addressing high priority objectives and activities that will be pursued over the next few years to reduce the risk of energy disruptions due to cyber incidents. because of the constantly changing threat and technology environments related to the digital.

Five Years Information Security Solution Planning Roadmap Templateо Powerpoint 6 month product roadmap template. download the 6 month product roadmap template for powerpoint. when to use this template: product managers and team leads can use this template to communicate a product’s high level goals, initiatives, and timeline over a six month period. this template is best suited for kickoff meetings, progress. A cyber security strategy includes an integrated strategy to reduce cyber risks by addressing high priority objectives and activities that will be pursued over the next few years to reduce the risk of energy disruptions due to cyber incidents. because of the constantly changing threat and technology environments related to the digital.

Comments are closed.