Five Years Information Security Solution Planning Roadmap Templateо

Five Years Information Security Solution Planning Roadmap Utilize our pre build five years information security solution planning roadmap template to present your plan of action in the most effective way. reduce the paperwork and showcase how different activities are linked to each other by incorporating this attention grabbing powerpoint theme. The intent of a roadmap is to document the activities projects by calendar year, typically three to five years. the focus of the activities is to meet the strategic objectives. the activities should include technology, processes, and or procedures and measures of success. 1.1.5 cyber security strategy maintenance.
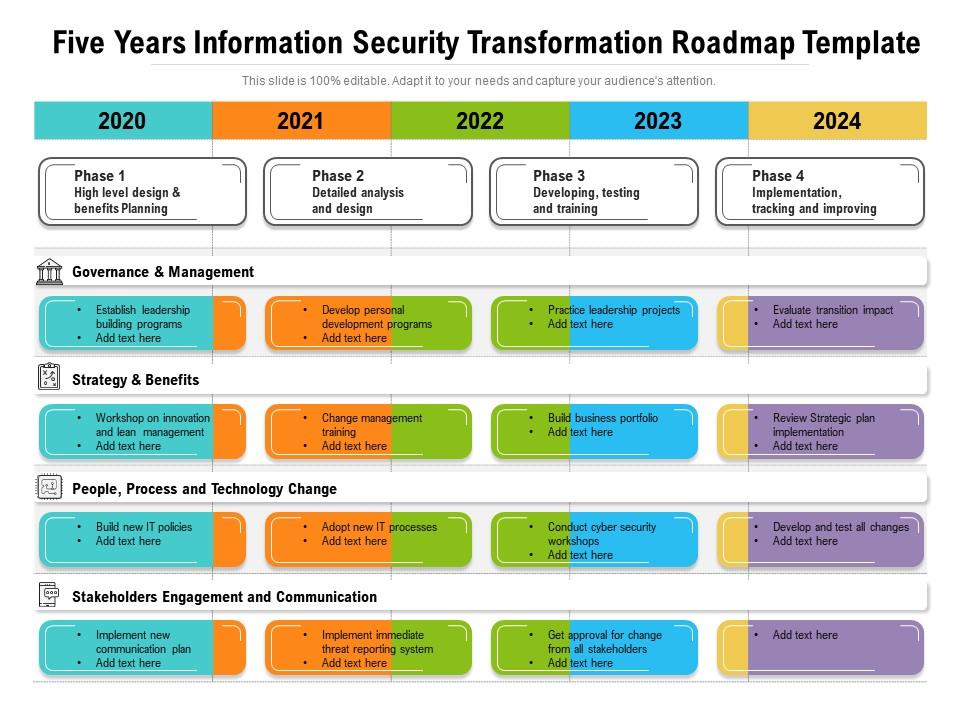
Five Years Information Security Transformation Roadmap Template Template 8 – information technology security roadmap for information technology security. here is a fantastic template that represents a strategy that needs to be incorporated for information technology security growth. with the help of this ppt framework, you can plan and accomplish your yearly goals, and arrange your entire workflow properly. A proven, structured approach to mature your information security program from reactive to strategic. a comprehensive set of tools to take the pain out of each phase in the strategy building exercise. visually appealing templates to communicate and socialize your security strategy and roadmap to your stakeholders. Presenting our innovatively structured five year information technology security roadmap for continuous threat analysis summary template. showcase your roadmap process in different formats like pdf, png, and jpg by clicking the download button below. this ppt design is available in both standard screen and widescreen aspect ratios. Examples include: summarize the assessment results in a “current state” document. then map the current state to the vision statement to identify gaps between them. the gap analysis will typically result in a list of projects and actions the cybersecurity program could take on in the coming year. some of the gaps will catalyze clear actions.

Comments are closed.