Generating Yara Rules By Classifying Malicious Byte Sequences

Generating Yara Rules By Classifying Malicious Byte Sequences Youtube While ml models for malware detection have become an industry standard for heuristically detecting malware, signature based detection still proliferates than. Explore a 27 minute black hat conference talk on developing an interpretable machine learning model for generating optimized malware detection signatures. dive into the process of creating yara rules by classifying malicious byte sequences, achieving high detection rates with minimal false positives.
Github Gradientjanitor Siglearn Code For Bh21 Talk Generating Yara On a corpus of malicious and benign elf executables targeting i386 and amd64, we observe detection rates in the 80% range with a false positive rate of 0% on the benign corpus with a few hundred yara rules.the approach is filetype agnostic and can be applied anywhere yara rules can be used whether it be simple static analysis of binaries. Code for bh21 talk: "generating yara rules by classifying malicious byte sequences" topics machinelearning yara yara rules security tools malware detection. You will need to swap the file name and yara rule file location name for the answer, not sure why it is like that but that is the format of the answer. once you have it properly figured out type. The main principle is the creation of yara rules from strings found in malware files while removing all strings that also appear in goodware files. therefore yargen includes a big goodware strings and opcode database as zip archives that have to be extracted before the first use. in version 0.24.0, yargen introduces an output option ( ai ).

8 13 Suppose We Are Generating Code For An Imperative Chegg You will need to swap the file name and yara rule file location name for the answer, not sure why it is like that but that is the format of the answer. once you have it properly figured out type. The main principle is the creation of yara rules from strings found in malware files while removing all strings that also appear in goodware files. therefore yargen includes a big goodware strings and opcode database as zip archives that have to be extracted before the first use. in version 0.24.0, yargen introduces an output option ( ai ). And in some cases, the only thing available is yara, the multiplatform classification tool maintained by virustotal. yara classifies content by applying yara rules –human readable rules that identify text artifacts associated with a specific type of malicious code or content. but writing hand crafted rules for yara can be time consuming, and. A specification and style guide for yara rules. introduction. yara is a powerful and versatile tool for malware detection, used by security researchers and analysts all over the world. yara rules are at the heart of this tool, providing a structured way to identify and classify malware based on various characteristics such as file names, sizes.
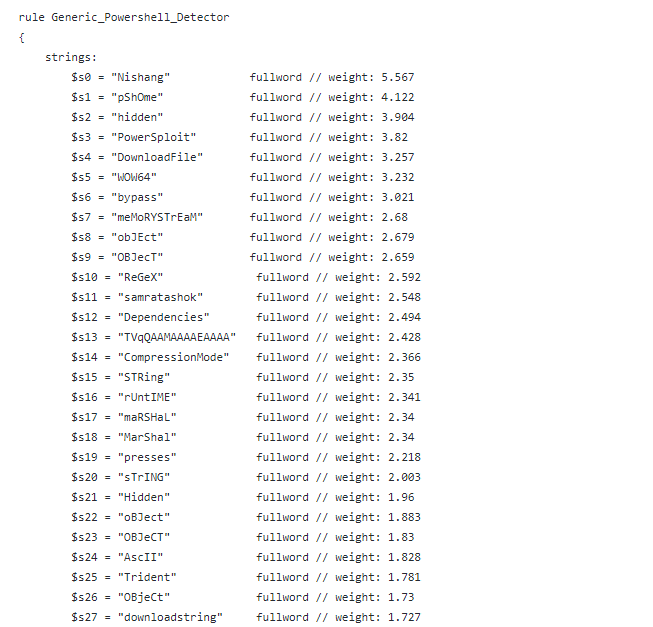
An Open Source Ml Toolkit For Automatically Generating Yara Rules And in some cases, the only thing available is yara, the multiplatform classification tool maintained by virustotal. yara classifies content by applying yara rules –human readable rules that identify text artifacts associated with a specific type of malicious code or content. but writing hand crafted rules for yara can be time consuming, and. A specification and style guide for yara rules. introduction. yara is a powerful and versatile tool for malware detection, used by security researchers and analysts all over the world. yara rules are at the heart of this tool, providing a structured way to identify and classify malware based on various characteristics such as file names, sizes.
Developing Yara Rules Based On Byte Patterns 0ffset

Comments are closed.