How To Ensure Network Security Logsign

Networking Support Of Azure For Sap Workloads A strong password should consist of at least 8 characters that involve upper and lower case letters, special characters, and numbers. in addition, employees should be obligatory to change passwords every three months or 90 days. using a multilayer security: multilayer security is the act of securing the network with a combination of multiple. Internet key exchange (also known as ike, ikev1 or ikev2) is a protocol that is used to generate a security association within the internet protocol security protocol suite. in this article, we will discuss internet key exchange in detail and explain why it is important for network security. if your job title requires a certain degree of.
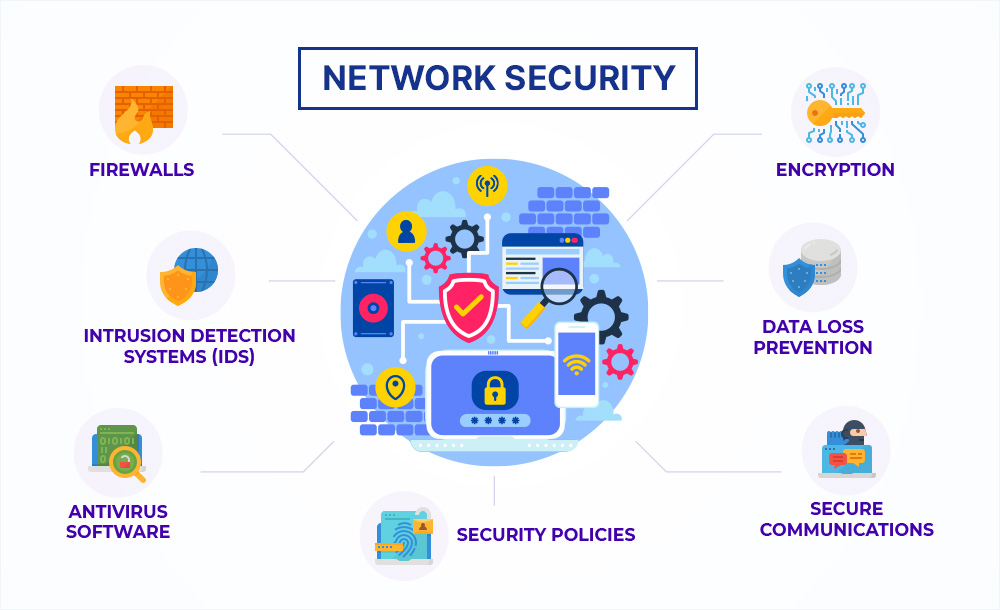
Network Security Images Simply put, the internet key exchange is a hybrid protocol that is often used for key management purposes in ipsec networks. it is often used as a method of exchanging encryption keys and or. There are various ways to detect suspicious ip addresses. you can use specifically designed software, use lookup and reputation tools or depend on a strong firewall. if you will be working with a. Conclusion. though data and sensitive information are vulnerable due to sophisticated cyber threats, the use of cryptography and pki can help organizations to conduct secure communication and transmission of such data and information. cryptography ensures data confidentiality, integrity, as well as authentication of only authorized users. Logsign's unified security operations platform offers a comprehensive solution for organizations to enhance their cybersecurity resilience, streamline threat detection, investigation, and incident response, and ensure compliance with regulations. the platform integrates multiple native logsign tools, including siem, threat intelligence, ueba.

How To Ensure Network Security Security Service Edge Conclusion. though data and sensitive information are vulnerable due to sophisticated cyber threats, the use of cryptography and pki can help organizations to conduct secure communication and transmission of such data and information. cryptography ensures data confidentiality, integrity, as well as authentication of only authorized users. Logsign's unified security operations platform offers a comprehensive solution for organizations to enhance their cybersecurity resilience, streamline threat detection, investigation, and incident response, and ensure compliance with regulations. the platform integrates multiple native logsign tools, including siem, threat intelligence, ueba. Network attacks are getting more complicated in today’s security environment. to obtain basic access information, attackers use various methods such as phishing attack or malware infection. after they enter the relevant it system, they disguise as the user with wide access authorization while trying to increase their privileges. 5 steps used by logsign siem to detect and stop the zero day attacks: detecting process of the zero day attacks begins with logsign siem correlation techniques by means of ti, web proxy, ad auth, dns server, ips, process events, and endpoint protection platform (epp) source logs. by means of correlation processes and behavior analysis, the user.

Premium Ai Image Encryption And Locking Ensure Network Security Privacy Network attacks are getting more complicated in today’s security environment. to obtain basic access information, attackers use various methods such as phishing attack or malware infection. after they enter the relevant it system, they disguise as the user with wide access authorization while trying to increase their privileges. 5 steps used by logsign siem to detect and stop the zero day attacks: detecting process of the zero day attacks begins with logsign siem correlation techniques by means of ti, web proxy, ad auth, dns server, ips, process events, and endpoint protection platform (epp) source logs. by means of correlation processes and behavior analysis, the user.

What Should Companies Do To Ensure Network Security Corporate

Comments are closed.