How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget
How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Practically every organization has internet connectivity and some form of it infrastructure, which means nearly all organizations are at risk of a cyber attack. to understand how great this risk is and to be able to manage it, organizations need to complete a cybersecurity risk assessment, a process.

How To Perform A Cybersecurity Risk Assessment In 5 Steps Techtarget To write an effective cyber risk statement, consider the following key steps: identify the risk. start by identifying potential cyber threats that put the business at risk. these can range from phishing attacks, malware and data breaches to insider threats and system outages. define the risk scenario. Examine all relevant cybersecurity materials to ensure the following five activities are performed in the event of a cyber attack: identify. perform a risk, threat and vulnerability assessment to identify potential threat actors and attack vectors. this step also helps determine how well the company is prepared to respond to attacks. Recognizing the types of data you hold and the sensitivity level of each sets the stage for your risk assessment. a data centric approach to cybersecurity flips the script. instead of a broad, one. 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization.

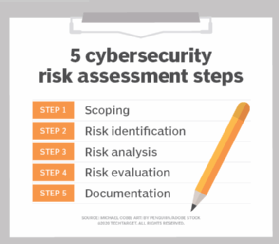
5 Steps To A Cyber Security Risk Assessment Hostingb2b Recognizing the types of data you hold and the sensitivity level of each sets the stage for your risk assessment. a data centric approach to cybersecurity flips the script. instead of a broad, one. 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization. A cybersecurity risk assessment improves the future security of an organization. however, it is a detailed and complex undertaking, which requires time and resources. a cybersecurity risk assessment comprises five major categories: scoping, risk identification, analysis, evaluation, and documentation. here is how you can go about the matter. determine the risk assessment scope before you. Include information about all stakeholders involved in the assessment process when defining the scope of your cybersecurity risk assessment. this typically means your it staff, management, legal and compliance teams, and, increasingly often, third party vendors of various software as a service (saas), infrastructure as a service (iaas), and platform as a service (paas) solutions.

How To Perform A Cybersecurity Risk Assessment A Step By Step Gu A cybersecurity risk assessment improves the future security of an organization. however, it is a detailed and complex undertaking, which requires time and resources. a cybersecurity risk assessment comprises five major categories: scoping, risk identification, analysis, evaluation, and documentation. here is how you can go about the matter. determine the risk assessment scope before you. Include information about all stakeholders involved in the assessment process when defining the scope of your cybersecurity risk assessment. this typically means your it staff, management, legal and compliance teams, and, increasingly often, third party vendors of various software as a service (saas), infrastructure as a service (iaas), and platform as a service (paas) solutions.

Comments are closed.