How To Perform A Cybersecurity Risk Assessment Template Checklist

How To Perform A Cybersecurity Risk Assessment Template Checklist Included with this guide are customizable reference tables (pages two, three, and four) to help organizations identify and document personnel and resources involved with each step of the assessment. while example entities and organizations are provided, customization is advised. 2. by conducting cyber risk assessments, public safety. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given.
Cybersecurity Risk Assessment Template For Creating Cybersecurity Use this cybersecurity risk assessment checklist template to meet your cybersecurity goals and implement a fail safe infosec plan. this unique template includes all 14 iso 27001 information security management steps, so you can account for and optimize all your security components (including application, information, network, end user, and. Your toolkit of free cybersecurity risk assessment templates. we understand the diverse needs of our audience, which is why we offer cybersecurity risk assessment templates in three different formats: 1. pdf template. ideal for those seeking a static format for printing or sharing digitally, our pdf template is secure and user friendly. 1) evaluate the scope of the risk assessment. as with most processes, the first step is to evaluate the scope of your assessment. you want to ensure that you cover all of the assets that could be at risk, but you don’t want to overdo it. think about how much of the organization you want to cover in the risk analysis and what type of assets. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment.
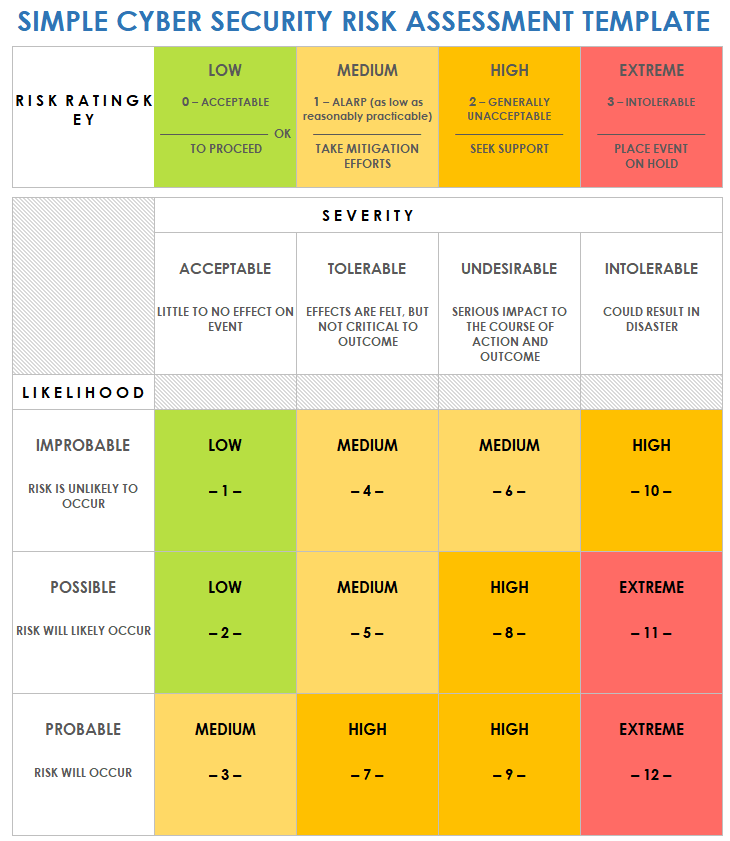
Free Cybersecurity Risk Assessment Templates Smartsheet 1) evaluate the scope of the risk assessment. as with most processes, the first step is to evaluate the scope of your assessment. you want to ensure that you cover all of the assets that could be at risk, but you don’t want to overdo it. think about how much of the organization you want to cover in the risk analysis and what type of assets. Step 2: identify and prioritize assets. the first step is to identify assets to evaluate and determine the scope of the assessment. this will allow you to prioritize which assets to assess. you may only want to assess some buildings, employees, electronic data, trade secrets, vehicles, and office equipment. A cybersecurity risk assessment evaluates an organization’s ability to identify, defend against and prioritize threats to its data and systems. the assessment involves identifying information security risks — threats that can potentially exploit your assets' vulnerabilities. every organization, regardless of size or sector, should conduct. 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization.
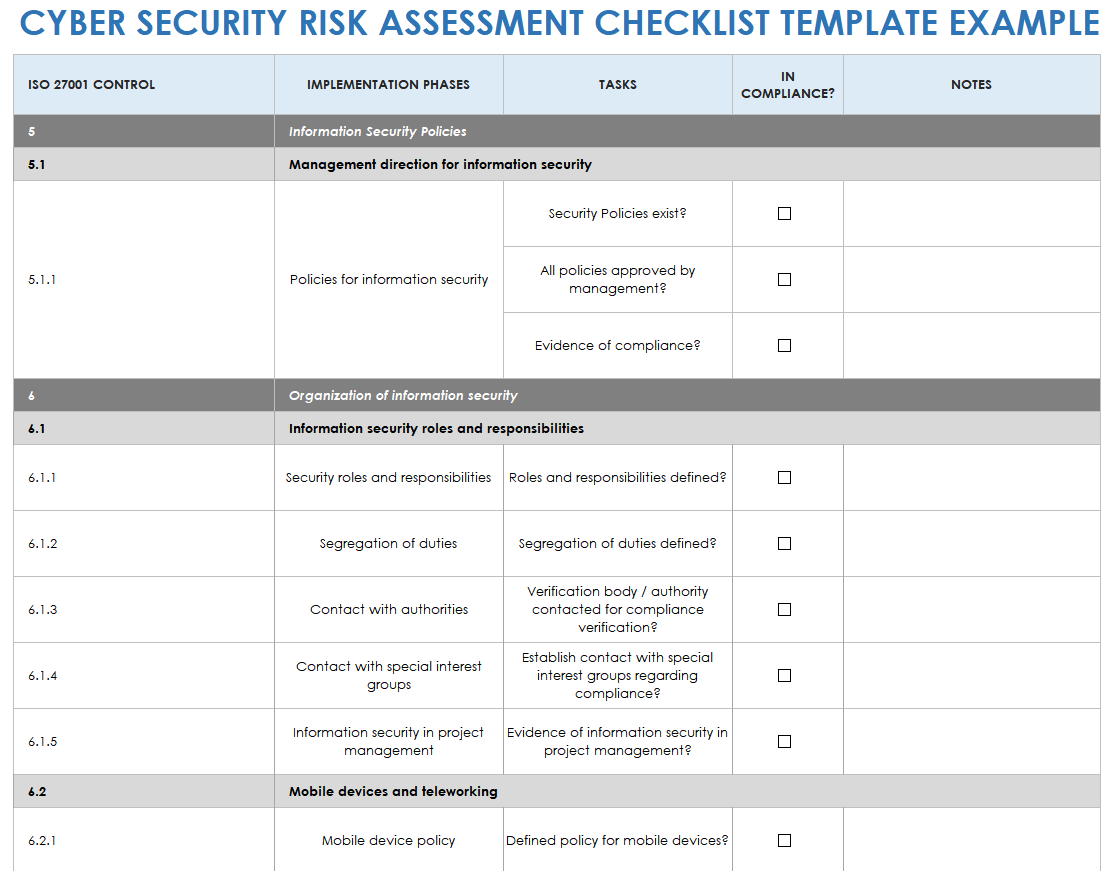
Free Cybersecurity Risk Assessment Templates Smartsheet A cybersecurity risk assessment evaluates an organization’s ability to identify, defend against and prioritize threats to its data and systems. the assessment involves identifying information security risks — threats that can potentially exploit your assets' vulnerabilities. every organization, regardless of size or sector, should conduct. 4. calculate the probability and impact of different cyber risks. two other important considerations for the risk assessment are: the probability of an attack, or the likelihood that an actor will exploit the vulnerability. the outcome of a potential attack, or the impact such an event will have on the organization.

Comments are closed.