Malware Analysis Pdf Analysis Youtube

Taosecurity Practical Malware Analysis Book Promotion Today we tackle the newest malware analysis exercise on the lets defend platform! this covers a possible malicious pdf file and answering 12 questions around. In this video, we are going to analyse a real pdf malware sample statically. this video gives an idea about how to understand how to proceed with analysing a.

Malware Analysis Pdf Analysis Youtube Learn the tools and techniques that can help you identify and analyze malicious pdf files start at 15:16 to jump into the details about static and dynamic. Receive video documentation channel ucnsdu 1ehxtgclimtvckhmq join do you need private cybersecurity training? sign up here m. Ring Ø labs: ringzerolabs how do you get started in #malware analysis and #reverseengineering? first, you need an analysis environment in place to. Detailed walkthrough of malware analysis on a suspicious pdf: step 1: collection of suspicious pdfs begin by obtaining a suspicious pdf document from a reliable source, such as a security research.

Malware Cosг Entrano Nei Nostri Dispositivi Riconoscere I Metodi Di Ring Ø labs: ringzerolabs how do you get started in #malware analysis and #reverseengineering? first, you need an analysis environment in place to. Detailed walkthrough of malware analysis on a suspicious pdf: step 1: collection of suspicious pdfs begin by obtaining a suspicious pdf document from a reliable source, such as a security research. We covered an overview of malware analysis, starting with basic static analysis and moving through to advanced static analysis techniques such as reverse eng. Check out this video on our channel about analyzing pdfs, where i cover the information in this blog as well as four examples of malicious pdfs that were used in real attacks. how pdf files get used to deliver malware. pdf files support a wide variety of data types that can be present (and not necessarily visible).
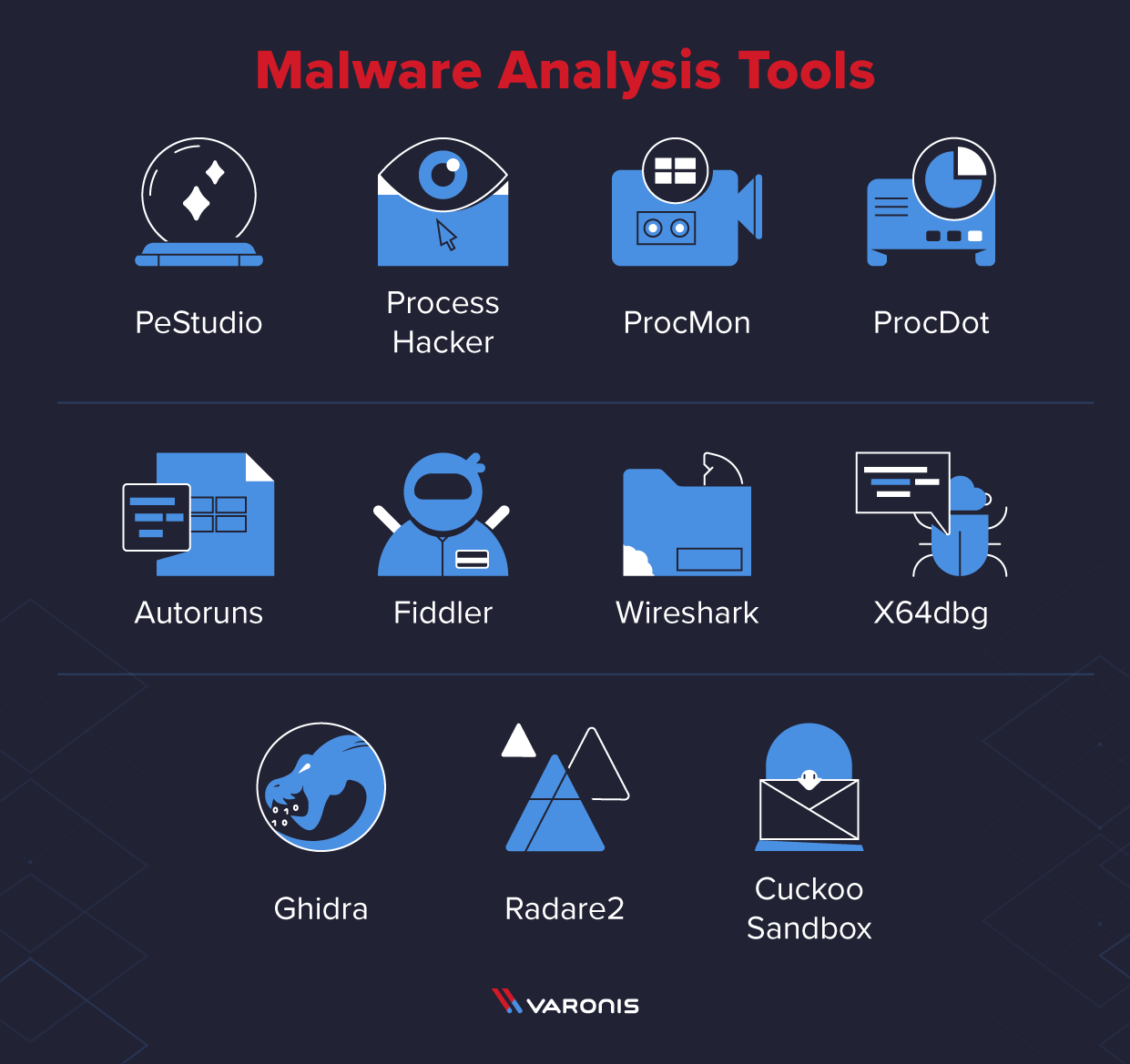
11 Best Malware Analysis Tools And Their Features We covered an overview of malware analysis, starting with basic static analysis and moving through to advanced static analysis techniques such as reverse eng. Check out this video on our channel about analyzing pdfs, where i cover the information in this blog as well as four examples of malicious pdfs that were used in real attacks. how pdf files get used to deliver malware. pdf files support a wide variety of data types that can be present (and not necessarily visible).

Comments are closed.