Microsoft Defender For Office 365 Best Practices Nsw It Support

Evaluate And Pilot Microsoft 365 Defender An Xdr Solution Microsoft Docs Defender for office 365 plan 1 provides all of these solutions as an add on. in plan 2, you will be able to discover and report on potential issues in your environment by leveraging tools such as threat tracker and explorer. in addition, you can use attack simulations to create malware phishing campaigns that keep users alert. Microsoft defender for office 365 plan 1 or plan 2 contain additional features that give more layers of security, control, and investigation. although we empower security administrators to customize their security settings, there are two security levels in eop and microsoft defender for office 365 that we recommend: standard and strict.

Microsoft Defender For Office 365 Security Overview Design Talk Connect microsoft defender for office 365 to sentinel. documentation in this format can be found under the step by step section in office 365 security. visit the docs by using aka.ms step by step. if there's a topic, task or config you'd like to see in this format, please let us know by leaving feedback. thank you!. An image of the start page for the microsoft defender for office 365 setup guide in the microsoft 365 admin center. follow zero trust cybersecurity principles, such as “assume breach.” basically, you proactively assume your systems have been breached and minimize the blast radius. The defender for office 365 secure architecture is designed to protect against echospoofing. in microsoft defender for office 365, you can send messages in various ways — either direct to an smtp endpoint or via connectors. in both cases, microsoft validates the sender of the message to ensure we process the message correctly or simply reject. Advanced cyberthreat hunting. automated investigation and response. cyberattack simulation training. microsoft defender xdr capabilities, such as cross domain hunting and incident correlation. use best in class microsoft security products to prevent and detect cyberattacks across your microsoft 365 workloads.

Microsoft Defender For Office 365 Workflow Features Plans The defender for office 365 secure architecture is designed to protect against echospoofing. in microsoft defender for office 365, you can send messages in various ways — either direct to an smtp endpoint or via connectors. in both cases, microsoft validates the sender of the message to ensure we process the message correctly or simply reject. Advanced cyberthreat hunting. automated investigation and response. cyberattack simulation training. microsoft defender xdr capabilities, such as cross domain hunting and incident correlation. use best in class microsoft security products to prevent and detect cyberattacks across your microsoft 365 workloads. Mastering configuration in defender for office 365 part sundeep saini on apr 29 2021 10:00 am. this blog is part two of a three part series on simplifying configuration of threat protection in office 365. 23.5k. Best practice: connect microsoft 365 detail: connecting microsoft 365 to defender for cloud apps gives you immediate visibility into your users' activities, files they are accessing, and provides governance actions for microsoft 365, sharepoint, onedrive, teams, power bi, exchange, and dynamics. for more information: connect apps.
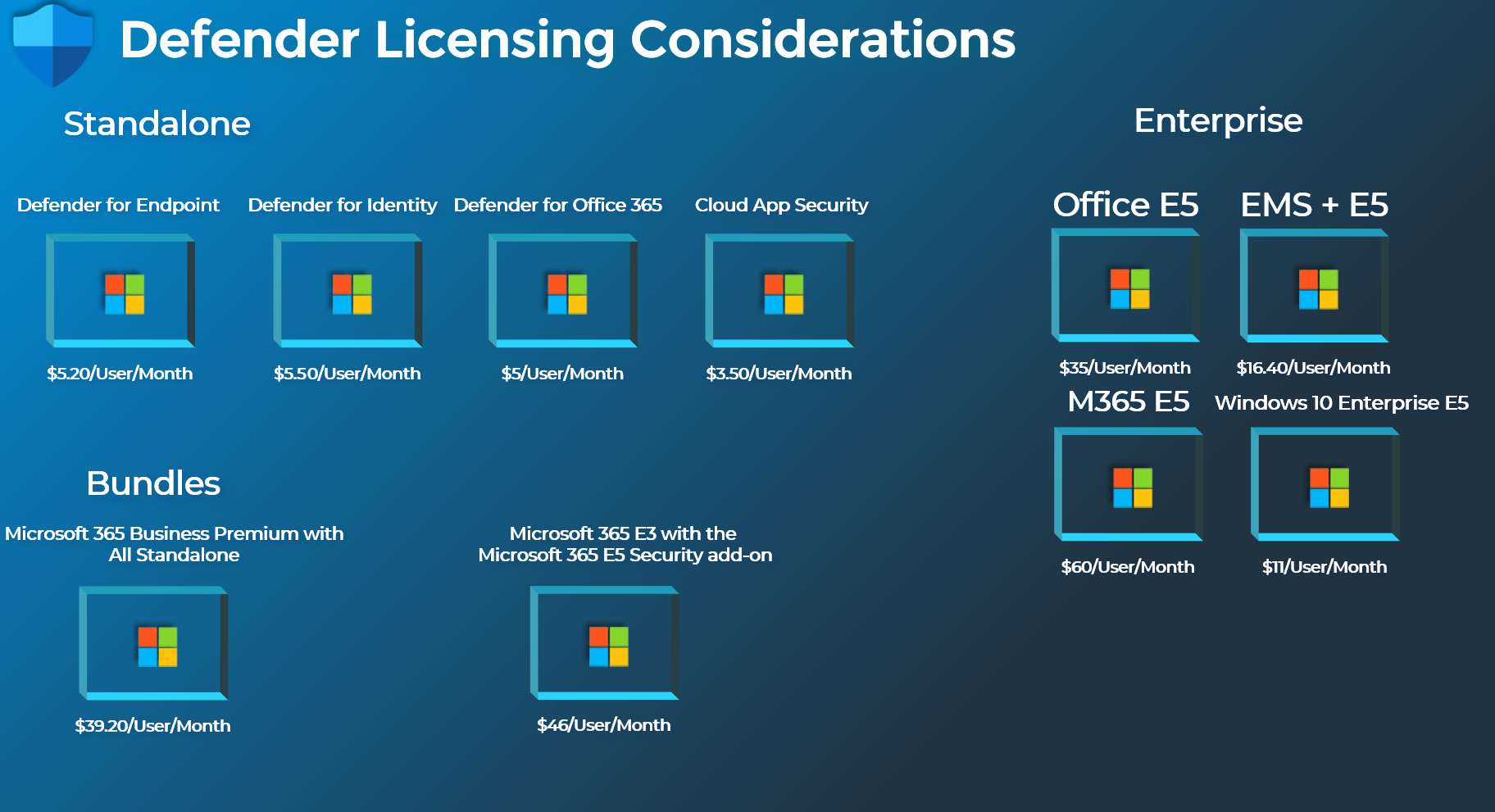
Microsoft Defender For Office 365 Security Overview Design Talk Mastering configuration in defender for office 365 part sundeep saini on apr 29 2021 10:00 am. this blog is part two of a three part series on simplifying configuration of threat protection in office 365. 23.5k. Best practice: connect microsoft 365 detail: connecting microsoft 365 to defender for cloud apps gives you immediate visibility into your users' activities, files they are accessing, and provides governance actions for microsoft 365, sharepoint, onedrive, teams, power bi, exchange, and dynamics. for more information: connect apps.

Comments are closed.