Radius Authentication Pros And Cons

Radius Authentication Pros And Cons Youtube In this video, learn about the pros and cons of using radius (remote authentication dial in user service). in this video, learn about the pros and cons of using radius (remote authentication. Pros & cons of tacacs pros of tacacs . increased security: tacacs encrypts all traffic between the client and server, which helps to protect user credentials and network traffic from unauthorized access. greater flexibility: tacacs allows for more granular authorization control than radius. this means that administrators can fine tune what.
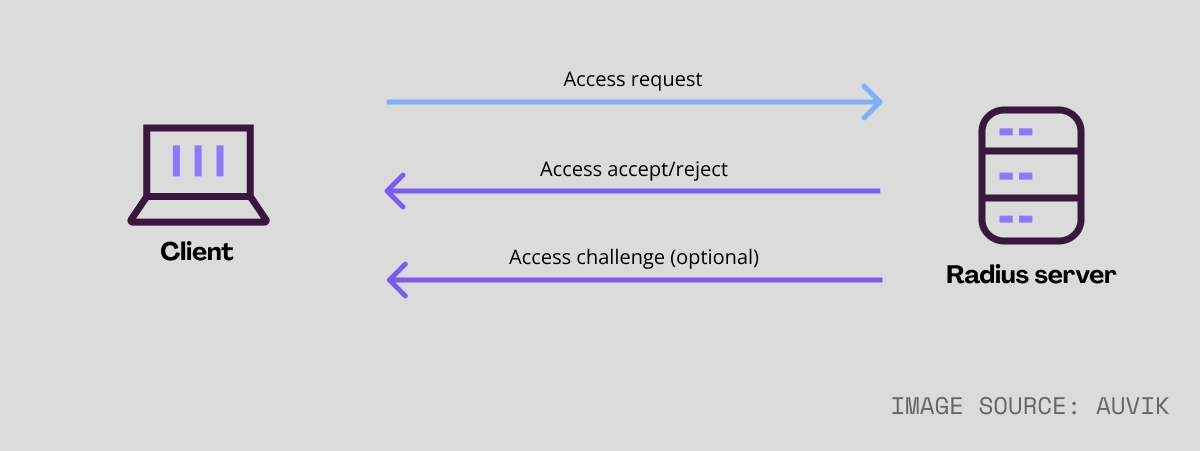
Network Authentication Protocols Types And Their Pros Cons Auvik The core details of radius. radius is an open standard aaa protocol that uses udp port 1645 or 1812 for authentication and udp port 1646 or 1813 for accounting. the fundamentals for the radius protocol are defined in its ratification as an internet engineering task force (ietf) accepted standard in 1997. to get into the nitty gritty of the. The most commonly used authorization and authentication protocols are oauth 2, tacacs , radius, kerberos, saml, and ldap active directory. it’s important to understand these are not competing protocols. i’ve seen many environments that use all of them simultaneously—they’re just used for different things. Radius authentication is a method employed to confirm a user’s identity when they endeavor to establish a connection with a network. here’s how it works: 1. user connection attempt. a user attempts to connect to a network or network resource, such as a vpn or wi fi access point. Radius is an open standard protocol that works with virtually all modern devices. tacacs is cisco’s proprietary protocol and works with cisco devices only. radius supports only one privilege level (limited to privilege mode) tacacs supports multiple privilege levels. radius supports 802.1x. port based network access control.

What Is Radius Protocol Radius authentication is a method employed to confirm a user’s identity when they endeavor to establish a connection with a network. here’s how it works: 1. user connection attempt. a user attempts to connect to a network or network resource, such as a vpn or wi fi access point. Radius is an open standard protocol that works with virtually all modern devices. tacacs is cisco’s proprietary protocol and works with cisco devices only. radius supports only one privilege level (limited to privilege mode) tacacs supports multiple privilege levels. radius supports 802.1x. port based network access control. As cyber security risks increase and secure access to network resources is required, organizations are adopting different authentication methods. radius certificate based authentication is one of those methods that increase the security level of the radius protocol. 80% of breaches in 2020 involved lost or stolen credentials or brute force. Pros: cons: radius is supported by a wide variety of network hardware and software vendors, ensuring flexibility and ease of integration in diverse it environments. while radius can serve small to medium sized deployments efficiently, it may face scalability issues in larger, more dynamic environments.

Comments are closed.