Securing Your Cloud Environment A Guide To Network Security In

Securing Your Cloud Environment A Guide To Network Security In This abstract provides an overview of ec council’s latest whitepaper, “securing your cloud environment: a guide to network security in virtualized it environments,” authored by vikas madaan. the whitepaper explores the key considerations and best practices for securing cloud environments, providing valuable insights for it professionals. The advantage of security policies is that they will auto enforce the compliance standard across the board in cloud deployments. 7. secure your containers. container security involves both container and orchestration platform protection, and kubernetes is the solution most often used in the cloud. you will need to create industry standard.
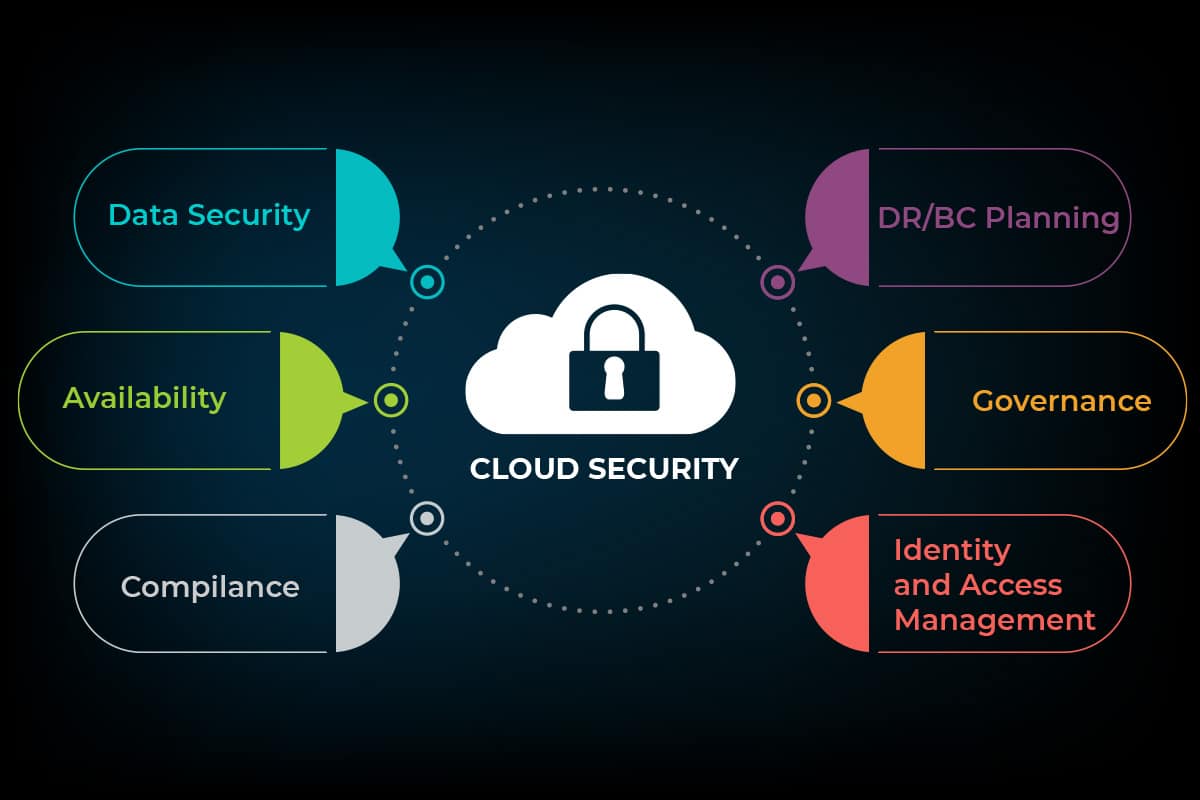
Cloud Security A Detailed Guide Ees Corporation Building secure networks in the cloud is fundamentally different from building them in a private, on premises environment. with secure networks in the cloud, the cloud provider handles certain tasks on your behalf, such as the management and governance of physical devices, their environment, or the security controls that surround them. The platform is free for the first 10 users and 10 devices. the full jumpcloud platform costs $15 per user per month. okta workforce identity: okta’s iam solution is most suitable for large. 10 best cnapp vendors in 2024. take advantage of ai driven threat protection and secure your cloud infrastructure right with cloud native application protection platforms (cnapps). top vendors like sentinelone, aqua security, cloudguard, and more provide real time threat detection, vulnerability assessment, and compliance monitoring for your. Cloud security encompasses the technologies, controls, processes, and policies which combine to protect your cloud based systems, data, and infrastructure. it is a sub domain of computer security and more broadly, information security. it is a shared responsibility between you and your cloud service provider.

Securing Cloud Environment вђ Cyber Security Networking Technology 10 best cnapp vendors in 2024. take advantage of ai driven threat protection and secure your cloud infrastructure right with cloud native application protection platforms (cnapps). top vendors like sentinelone, aqua security, cloudguard, and more provide real time threat detection, vulnerability assessment, and compliance monitoring for your. Cloud security encompasses the technologies, controls, processes, and policies which combine to protect your cloud based systems, data, and infrastructure. it is a sub domain of computer security and more broadly, information security. it is a shared responsibility between you and your cloud service provider. Central to any cloud security strategy is the protection of sensitive data stored and processed within your cloud environments. this entails employing encryption, access controls, and data loss prevention mechanisms to safeguard data at rest, in transit, and during processing. additionally, it’s important to establish data discovery and. The network owner, on the other hand, is responsible for securing anything they put on that cloud environment. many people worry about giving up control of securing the hardware and data centers, but established public cloud service providers like amazon, microsoft, and google can devote more resources to things like physical security.

Securing Your Cloud Environment Best Practices And Strategies Central to any cloud security strategy is the protection of sensitive data stored and processed within your cloud environments. this entails employing encryption, access controls, and data loss prevention mechanisms to safeguard data at rest, in transit, and during processing. additionally, it’s important to establish data discovery and. The network owner, on the other hand, is responsible for securing anything they put on that cloud environment. many people worry about giving up control of securing the hardware and data centers, but established public cloud service providers like amazon, microsoft, and google can devote more resources to things like physical security.

Comments are closed.