Understanding Authentication In Networking Network Encyclopedia

Understanding Authentication In Networking Network Encyclopedia Understanding what authentication is and how it operates within the networking landscape is essential for anyone involved in managing or securing digital systems. this article aims to unpack the intricacies of authentication, exploring its methods, protocols, and the critical role it plays in maintaining the integrity of networked systems. Basic authentication is a method used in http for an application or a web server to request a username and password from a client. the credentials are then sent across the network as part of the http request header. transmission process: the credentials are encoded using base64, a binary to text encoding scheme.

Understanding Xid Response Frames In Networking Network Encyclopedia The extensible authentication protocol (eap) stands as a foundational framework for network access security, providing the flexibility to support various authentication methods. initially conceived to facilitate authentication for network access connections, eap has evolved to become integral in securing modern digital communications. this. Personal computers, wireless networks, wireless access points, databases, webpages, and other network based services and apps might all fall under this category. upon successful authentication, a person or process is often put through an authorization procedure to decide if they should be granted access to a certain protected resource or system. Understanding network authentication methods n able. rmm for growing msps and it teams managing complex networks. all in one rmm for it service providers seeking quick time to value. multi tenant solution to manage, secure, and automate microsoft 365, azure resources, and intune. cloud first backup and disaster recovery for servers. Credit: silberfuchs. certificate based authentication is a cryptographic technique that allows one computer to securely identify itself to another across a network connection, using a document.
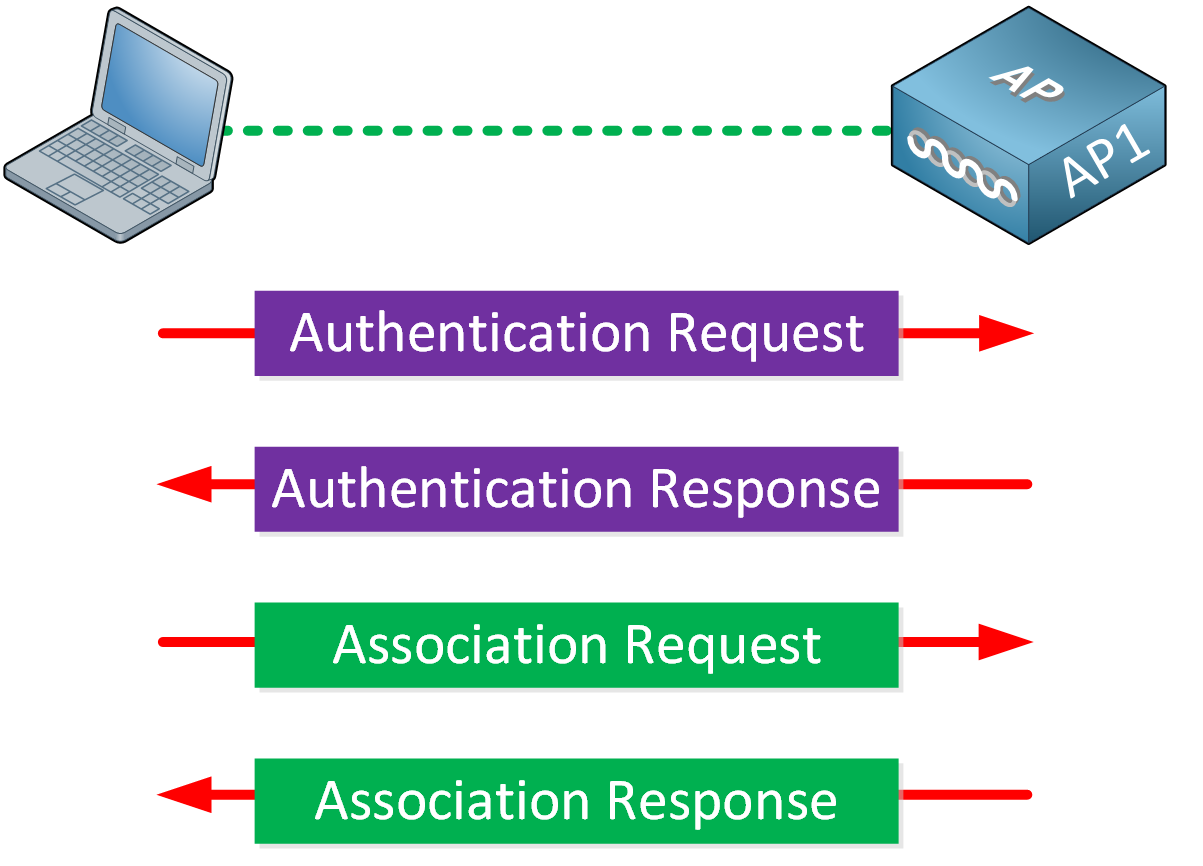
Wi Fi Legacy Security Mechanisms Understanding network authentication methods n able. rmm for growing msps and it teams managing complex networks. all in one rmm for it service providers seeking quick time to value. multi tenant solution to manage, secure, and automate microsoft 365, azure resources, and intune. cloud first backup and disaster recovery for servers. Credit: silberfuchs. certificate based authentication is a cryptographic technique that allows one computer to securely identify itself to another across a network connection, using a document. Authentication is an absolutely essential element of a typical security model. it is the process of confirming the identification of a user (or in some cases, a machine) that is trying to log on. Authentication protocol that restricts unauthorized clients from connecting to a lan through publicly accessible ports. an authentication server validates each supplicant (client) connected to an authenticator (network access switch) po rt before making available any se rvices offered by the switch or the lan.

Comments are closed.