What Is Challenging Malware Analysis New York Tech Media
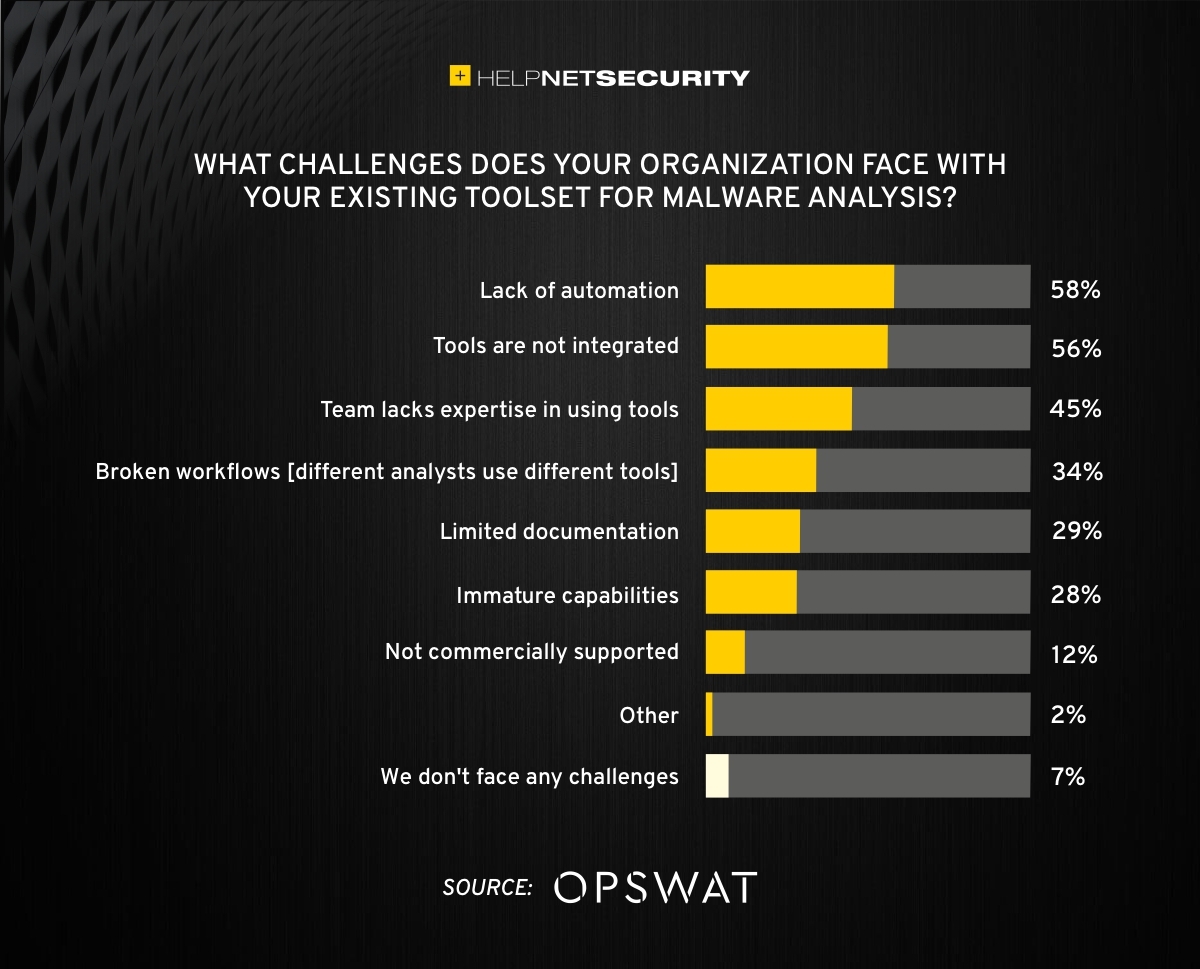
What Is Challenging Malware Analysis New York Tech Media Malware analysis is the process of examining malware to determine how it got past defenses and what it was designed to do once inside an environment. malware analysts are the brains behind the operation. while an interesting and in demand occupation, it isn't always easy. to help new and experienced analysts alike, authors amr thabet and alexey. Challenges in malware analysis. program analysis is a challenging task when source code is available. it is even more challenging when analyzing malware where neither the source code nor debug information are present. malware authors often employ a myriad of evasion techniques to impede automated reverse engineering and static analysis efforts.

What Is Challenging Malware Analysis New York Tech Media Malware analysis definition. malware analysis is the study of the unique features, objectives, sources, and potential effects of harmful software and code, such as spyware, viruses, malvertising, and ransomware. it analyzes malware code to understand how it varies from other kinds. below is a malware analysis guide to help you better understand. Malware detection and analysis: challenges and research. opportunities. zahid akhtar. department of network and computer security, state university of new y ork polytechnic institute, usa. email. Malware analysis can reveal the unique features and variations of different types of malware such as viruses, worms, trojans, rootkits, backdoors, spyware, malvertising, and ransomware. this knowledge can help organizations to develop effective countermeasures and improve the overall security of their systems. Malware analysis is the process of detecting and mitigating possible risks in a website, application, or server by investigating the unique characteristics, intentions, sources, and potential impacts of malicious software like malware, viruses, malware advertising, spyware, and other types of code.

Comments are closed.