What Is Osint In Cyber Security How To Use Osint Techniques
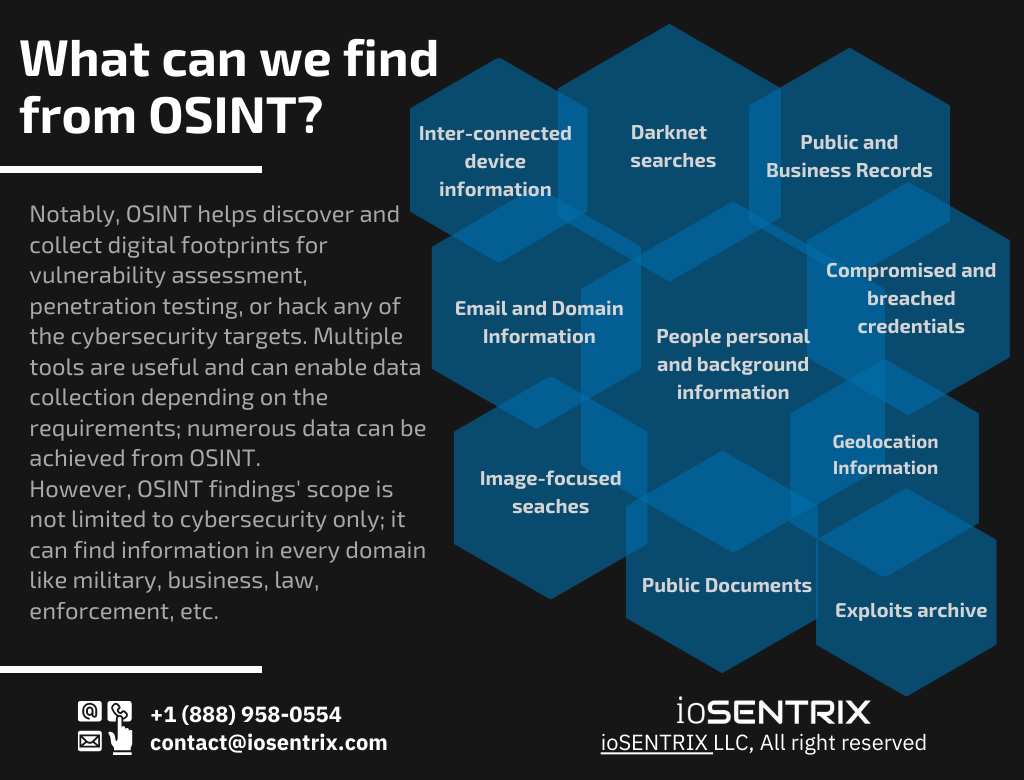
How Osint Is Used In Cybersecurity Part One Iosentrix Osint skills are the abilities and knowledge necessary to collect, analyze, and use information from open sources for various purposes. these skills can be applied in fields such as intelligence, security, and law enforcement, as well as in other areas where access to information is important. some of the key osint skills include: understanding. Open source intelligence (osint) is the process of gathering and analyzing publicly available information to assess threats, make decisions or answer specific questions. many organizations use osint as a cybersecurity tool to help gauge security risks and identify vulnerabilities in their it systems. cybercriminals and hackers also use osint.

How Osint Is Used In Cybersecurity Part Two Iosentrix Vrogue Co Cybersecurity, the osint lifecycle & “finished intelligence”. open source intelligence (osint) is a systematic process within cybersecurity, evolving through distinct stages to transform raw data into actionable insights. the osint lifecycle encompasses five crucial stages, each contributing to the generation of “finished intelligence.”. Osint operations, whether practiced by it security pros, malicious hackers, or state sanctioned intelligence operatives, use advanced techniques to search through the vast haystack of visible data. Osint helps security teams unearth clues that individuals leave in the open that compromise security. like using a vulnerability scanner to find flaws in systems, osint tools pick up on problem data, such as dates of birth, social security numbers, family members or even hobbies that could help attackers compromise an account. osint techniques. Open source intelligence (osint) is a critical tool used by cybersecurity professionals to identify compromised credentials, potential vulnerabilities within organizations, and overall cyber risks. it facilitates timely detection of sensitive data exposure , allowing cybersecurity teams to implement quick responses including security patches.

Comments are closed.